2
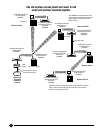
Access Point with Switch
Want to connect a wireless
LAN to a wired LAN? Choose the
Access Point with Switch
(LW6004A). It lets any 802.11g or
802.11b compliant PC join the
wireless network. This integral
switch with five LAN connections
enables wired devices, segments,
or entire networks to communi-
cate with your wireless WAN.
The access point supports
Web-based configuration. It has a
built-in DHCP server to allow
multiple wireless and wired users
to get their IP address
automatically.
With the access point’s ESSID
authentication, 64-, 128-, and
152-bit WEP encryption and MAC
address filtering, you can prevent
unauthorised wireless stations
from accessing your wireless
network.
The AP also includes a
2.2-dBm dipole antenna.
Wireless Router
The Pure Networking 802.11g
Wireless Router (LW6005A)
allows you to share the Internet
among one WAN connection and
up to four LAN connections via
one ADSL or cable modem.
The router gives you high
Internet access throughput (up
to 50 Mbps) and supports up to
253 users. It includes four
10-/100-Mbps LAN ports and one
10-/100-Mbps WAN port.
Special applications, DMZ,
virtual servers, access control,
firewall, and bridge mode are also
supported. You can monitor the
router’s status via DHCP client
log, security log, and device/
connection status. Or configure it
remotely via its Web-based
Graphical User Interface (GUI).
Client users are required to
get authorisation before
connecting to access points (APs)
or AP routers, and the data
transmitted in the network is
encrypted/decrypted by a
dynamically changed secret key.
Automatic fallback also increases
data security and reliability.
8-dBi Omnidirectional Antenna and
14-dBi Directional Panel Antenna
If you need to increase the
transmitting and receiving power
of your wireless access point or
router, order one of our 2.4-GHz
Antennas. There’s an 8-dBi
Omnidirectional model (LW6200A)
and a 14-dBi Directional Panel
model (LW6201A).
Choose the omnidirectional
model when you have several
access points that you want to
connect together with a clear
line-of-sight in multiple directions
from the main access point.
Select the directional panel
model when you need to connect
just two access points or routers
together with a clear line-of-sight.
You can also use the directional
panel at a remote site where the
access point is configured as a
bridge connecting a remote LAN
via wireless to the main office.
This not only increases the
distance from the remote site to
the main office, but also cuts
down on interference.
Choose the operating mode
When you’re using the Pure
Networking 802.11g Wireless
Adapters, access points, or
routers, two operating modes are
possible.
Ad-hoc mode allows you to
connect to another wireless
station in the wireless LAN
network without an access point
or router. Typically, you’d have a
group of PCs with wireless links to
each other in a small office or
home environment (SOHO). Each
PC would contain a wireless
adapter (PCMCIA, PCI, or USB).
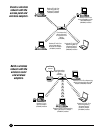
More complicated applica-
tions require an access point or
router. Suppose, for example, that
you want to link a wireless
network to a wired network.
When you connect a wireless
LAN and a combination (wireless
and wired) LAN together, it’s
called an infrastructure
configuration. Infrastructure
mode requires an 802.11 access
point. This mode is used on an
enterprise scale for wireless
access to a central database, or
for a wireless application for
mobile workers.
Keep your network safe and secure
When you have a wireless
network, security is a big
concern. You don’t want the
wireless signals to be intercepted
and sent to someone else’s
wireless device. Our wireless
adapters, switches, and routers
encrypt data for superior security
using WEP, TKIP, and AES.
(Windows 98 SE, Me, and
Windows NT use these three
types of security.)
WEP is Wired Equivalent
Privacy, a data privacy
mechanism based on a 40-bit
shared key algorithm, as
described in the IEEE 802.11
standard.
TKIP is a quick-fix method to
quickly overcome the inherent
weaknesses in WEP security,
especially the reuse of encryption
keys. TKIP is involved in the IEEE
802.11i WLAN security standard.
AES (Advanced Encryption
Standard), a chip-based security,
has been developed to ensure the
highest degree of security and
authenticity for digital information
that‘s in transit across the
network or stored. This standard
makes more efficient use of
hardware and/or software than
previous encryption standards.
AES is also included in the IEEE
802.11i standard.
Compared with AES, TKIP is a
temporary protocol for replacing
WEP security until manufacturers
implement AES at the hardware
level.
Another way to protect your
network from intruders is
authentication. Three
authentication modes are
possible: None, Shared, or WPA-
PSK.
Windows XP and Windows
2000 use two types of
authentication for the wireless
device (adapter, switch, or router)
in a home (WPA-PSK, no server)
or enterprise (WPA, with server).
WPA-PSK is a special mode
designed for home and small-
business users who do not have
access to network authentication
servers. In this mode, known as
Pre-Shared Key, you manually
enter the starting password in the
access point or gateway, as well
as in each wireless station in the
network. WPA takes over
automatically from that point,
keeping unauthorised users that
don’t have a matching password
from joining the network while
encrypting the data traveling
between authorised devices. The
encryption methods include TKIP
and AES.
Configuration is easy
All of the wireless devices
include a configuration utility.
This powerful application helps
you configure the adapter, switch,
or router, and monitor the link
status and statistics during the
communication process.
Technically Speaking