PowerConnect B-Series FCX Configuration Guide 1219
53-1002266-01
How 802.1X port security works
34
Client/Supplicant – The device that seeks to gain access to the network. Clients must be running
software that supports the 802.1X standard (for example, the Windows XP operating system).
Clients can either be directly connected to a port on the Authenticator, or can be connected by way
of a hub.
Authentication server – The device that validates the Client and specifies whether or not the Client
may access services on the device. Dell supports Authentication Servers running RADIUS.
Communication between the devices
For communication between the devices, 802.1X port security uses the Extensible Authentication
Protocol (EAP), defined in RFC 2284. The 802.1X standard specifies a method for encapsulating
EAP messages so that they can be carried over a LAN. This encapsulated form of EAP is known as
EAP over LAN (EAPOL). The standard also specifies a means of transferring the EAPOL information
between the Client/Supplicant, Authenticator, and Authentication Server.
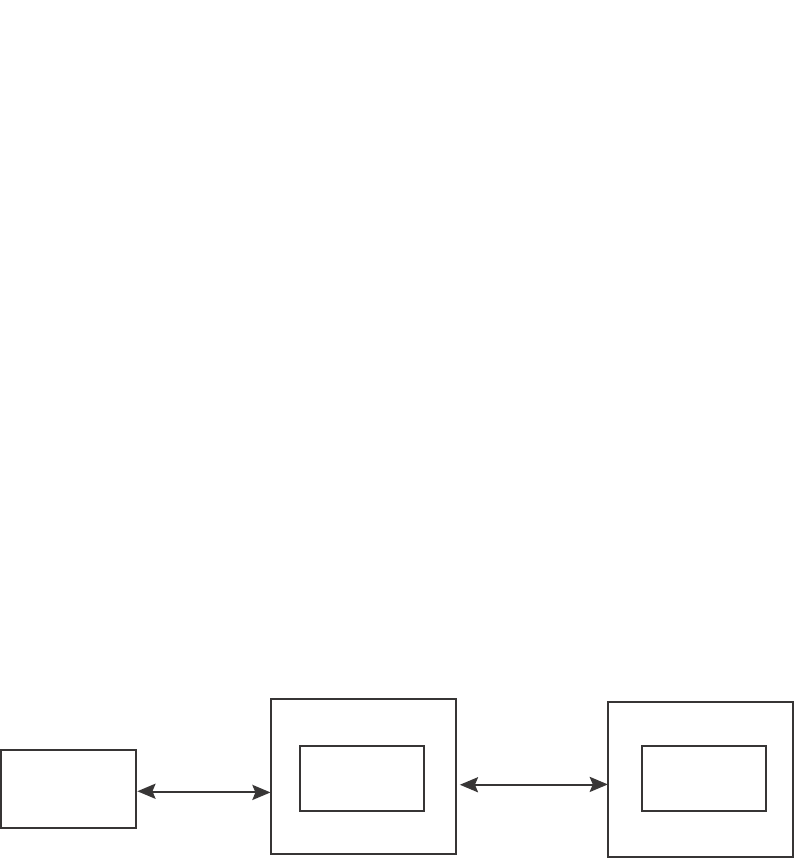
EAPOL messages are passed between the Port Access Entity (PAE) on the Supplicant and the
Authenticator. Figure 154 shows the relationship between the Authenticator PAE and the
Supplicant PAE.
FIGURE 154 Authenticator PAE and supplicant PAE
Authenticator PAE – The Authenticator PAE communicates with the Supplicant PAE, receiving
identifying information from the Supplicant. Acting as a RADIUS client, the Authenticator PAE
passes the Supplicant information to the Authentication Server, which decides whether the
Supplicant can gain access to the port. If the Supplicant passes authentication, the Authenticator
PAE grants it access to the port.
Supplicant PAE – The Supplicant PAE supplies information about the Client to the Authenticator
PAE and responds to requests from the Authenticator PAE. The Supplicant PAE can also initiate the
authentication procedure with the Authenticator PAE, as well as send log off messages.
Controlled and uncontrolled ports
A physical port on the device used with 802.1X port security has two virtual access points a
controlled port and an uncontrolled port. The controlled port provides full access to the network.
The uncontrolled port provides access only for EAPOL traffic between the Client and the
Authentication Server. When a Client is successfully authenticated, the controlled port is opened to
the Client. Figure 155 illustrates this concept.
Authentication
Server
RADIUS
Messages
Authenticator
PAE
Switch
(Authenticator)
Supplicant
PAE
802.1X-Enabled
Supplicant
EAPOL
Messages


















