11.1 Conditions and limitations of antivirus scan
161
(see chapter 12.3). This implies that the antivirus check is limited by the following
factors:
• Antivirus check cannot be used if the traffic is transferred by a secured channel
(SSL/TLS). In such a case, it is not possible to decipher traffic and separate trans-
ferred objects.
• Within email antivirus scanning (SMTP and POP3 protocols), the firewall only removes
infected attachments — it is not possible to drop entire email messages. In case of
SMTP protocol, only incoming traffic is checked (i.e. traffic from the Internet to the
local network — incoming email at the local SMTP server). Check of outgoing traffic
causes problems with temporarily undeliverable email.
For details, see chapter 11.4.
• Object transferred by other than HTTP, FTP, SMTP and POP3 protocols cannot be
checked by an antivirus.
• If a substandard port is used for the traffic, corresponding protocol inspector will
not be applied automatically. In that case, simply define a traffic rule which will allow
this traffic using a corresponding protocol inspector (for details, see chapter 6.3).
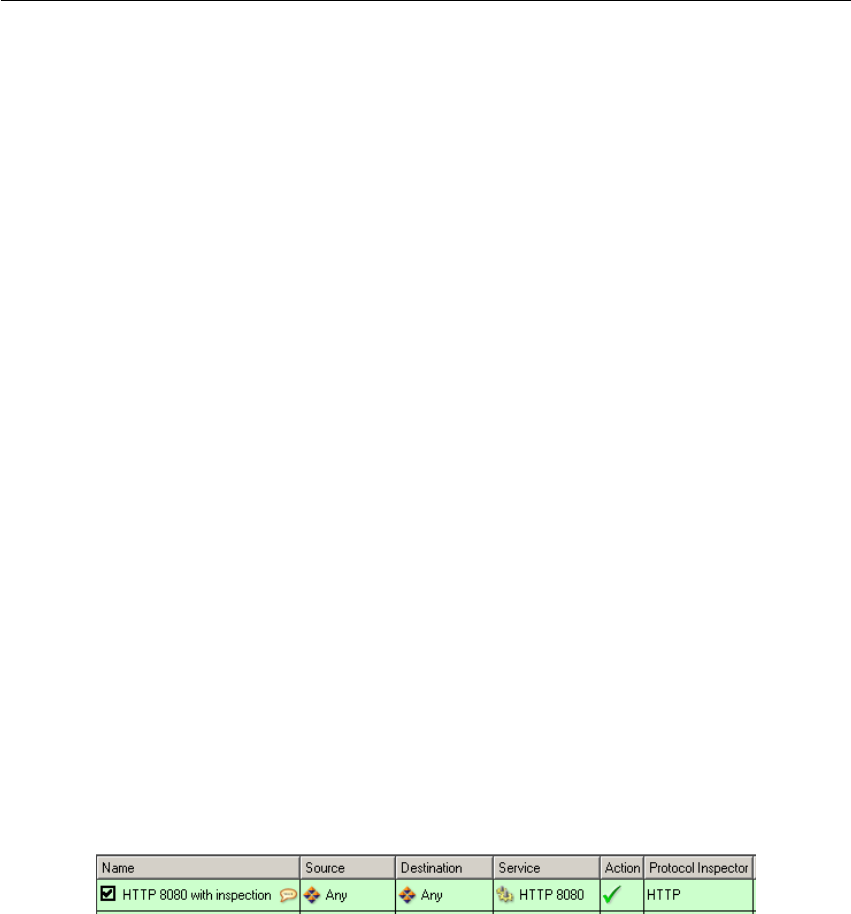
Example: You want to perform antivirus checks of the HTTP protocol at port 8080.
1. Define the HTTP 8080 service (TCP protocol, port 8080).
2. Create a traffic rule which will allow this service applying a corresponding proto-
col inspector.
Figure 11.1 Traffic rule for HTTP protocol inspection at non-standard ports
Add the new rule before the rule allowing access to any service in the Internet (if
such a rule exists). If the NAT (source address translation) technology is used for
Internet connection, address translation must be set for this rule as well.
Note: A corresponding protocol inspector can be also specified within the ser-
vice definition, or both definition methods can be used. Both methods yield the
same result, however, the corresponding traffic rule is more transparent when
the protocol inspector is defined in it.