y Key:
Show the key value of the aggregator. The key value is determined by the LACP protocol entity and
can’t be set through management.
y Trunk Status:
Show the trunk status of a single member port.”---“ means “not ready”
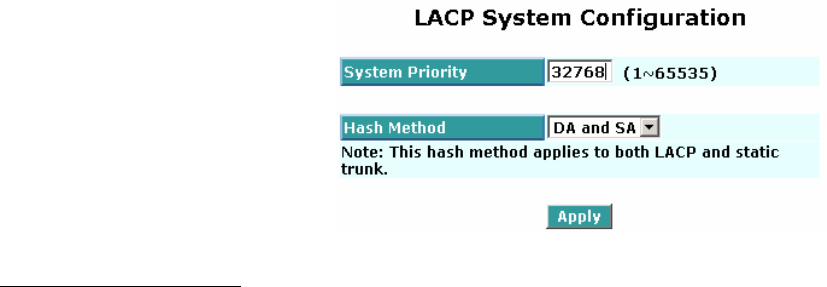
3.13.3 LACP System Config
It is used to set the priority part of the LACP system ID. LACP will only aggregate together the ports whose
peer link partners are all on a single system. Each system supports LACP will be assigned a globally unique
System Identifier for this purpose. A system ID is a 64-bit field comprising a 48-bit MAC Address and 16-bit
priority value.
Parameter description:
y System Priority:
The System Priority can be set by the user. Its range is from 1 to 65535. Default: 32768.
y Hash Method:
DA+SA, DA and SA are three Hash methods offered for the Link Aggregation of the switch. Packets
will decide the path to transmit according to the mode of Hash you choose.
Default: DA and SA
3.14 802.1x Configuration
802.1x port-based access control provides a method to restrict users to access network resources via
authenticating user’s information. This restricts users from gaining access to the network resources through a
802.1x-enabled port without authentication. If a user wishes to touch the network through a port under 802.1x
control, he (she) must firstly input his (her) account name for authentication and waits for gaining authorization
before sending or receiving any packets from a 802.1x-enabled port.
Before the devices or end stations can access the network resources through the ports under 802.1x control,
the devices or end stations connected to a controlled port send the authentication request to the authenticator,
the authenticator pass the request to the authentication server to authenticate and verify, and the server tell
the authenticator if the request get the grant of authorization for the ports.
According to IEEE802.1x, there are three components implemented. They are Authenticator, Supplicant and
Authentication server shown below.
44


















