234
SSH
SSH
Overview
The IOLAN contains SSH Server software that you need to configure if the IOLAN is going to be
accessed via SSH. If you specify more than one
Authentication method and/or Cipher, the IOLAN
will negotiate with the client and use the first authentication method and cipher that is compatible
with both systems.
Functionality
When you are using the SSH connection protocol, keys need to be distributed to all users and the
IOLAN. Below are a couple of example scenarios for key/certificate distribution.
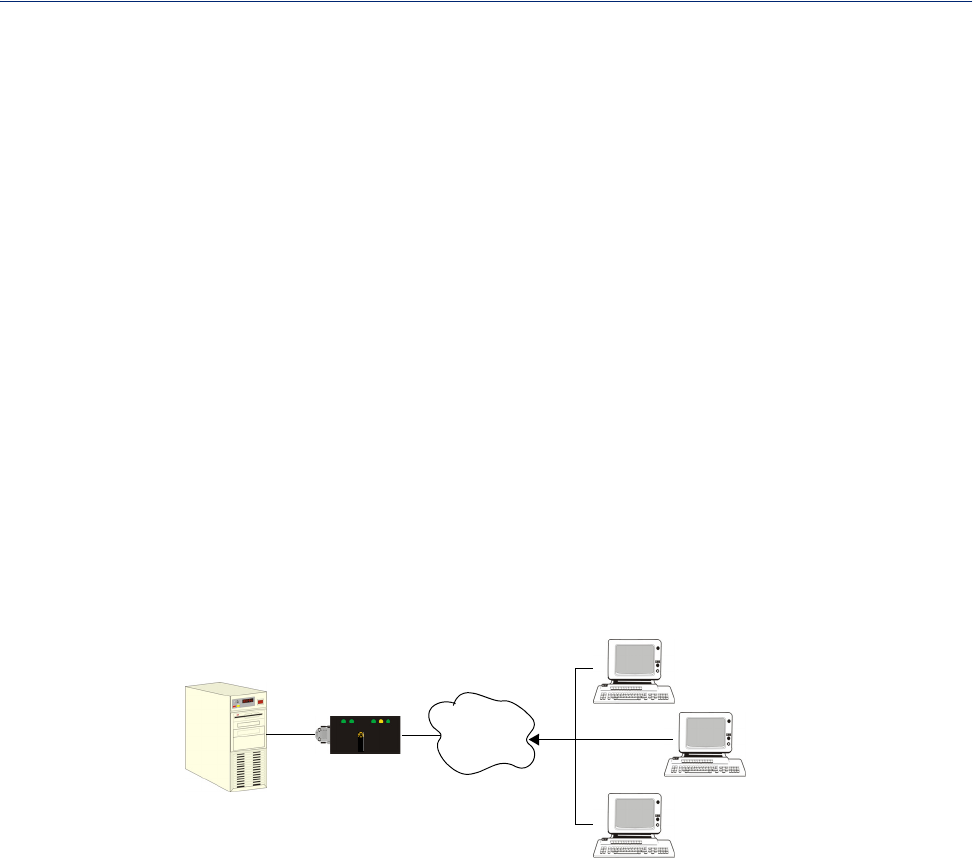
Users Logging into the IOLAN Using SSH
This scenario applies to serial ports configured for Console Management using the SSH protocol. In
the following example, users are connecting to the IOLAN via SSH from the LAN. Therefore, the
following keys need to be exchanged:
z Upload the IOLAN SSH Public Key to each user’s host machine who is connecting and logging
into the IOLAN using SSH.
z Download the SSH Public Key from each user’s host machine who is connecting and logging
into the IOLAN using SSH.
Device Server
Server
perle
Network
Lynn
Tracy
Dennis
Device Server Public Key
Lynn Private Key
Device Server Public Key
Tracy Private Key
Device Server Public Key
Dennis Private Key
Device Server Private Key
Lynn Public Key
Tracy Public Key
Dennis Public Key
SSH