`
`
3
Getting Critical Information
Into The Right Hands
Business runs on information.
That information, however, must be
managed and protected. Liebert
offers the tools to keep the people
on the front line — such as IT,
network, data center and facility
managers — informed as to the
status of their critical systems. By
utilizing a network infrastructure
approach to monitoring, Liebert
has the solutions that align a
customer's needs for real-time
knowledge and system flexibility
with critical system uptime and
capital allocation constraints.
This type of system can provide
the information you need to
manage your critical equipment,
giving you a variety of ways to
receive and manage this
data — through computers at
your site or even on the web via
standard browser software.
From the traditional centralized
data center to constantly evolving
distributed network topologies,
Liebert has the solutions that
provide just the right amount of
control, monitoring, and protection
for your critical space requirements.
The Importance Of Support
System Monitoring
The reliability of your computing
and communications systems is
a direct result of the reliability of the
power and environmental systems
that help maintain their proper
operation. That's why Liebert is so
firmly committed to providing
monitoring capability in our
products. No one knows more about
what it takes to collect and deliver
the vital information you need to
manage your critical support systems.
To protect your critical business systems, it is important that
we first understand how you and your customers utilize these
resources. Knowing how your network is used allows us to
design system protection that addresses your real world needs.
To maintain the high level of availability that users expect, your
monitoring system must be able to keep you up-to-date on
any changes in the condition of your network infrastructure.
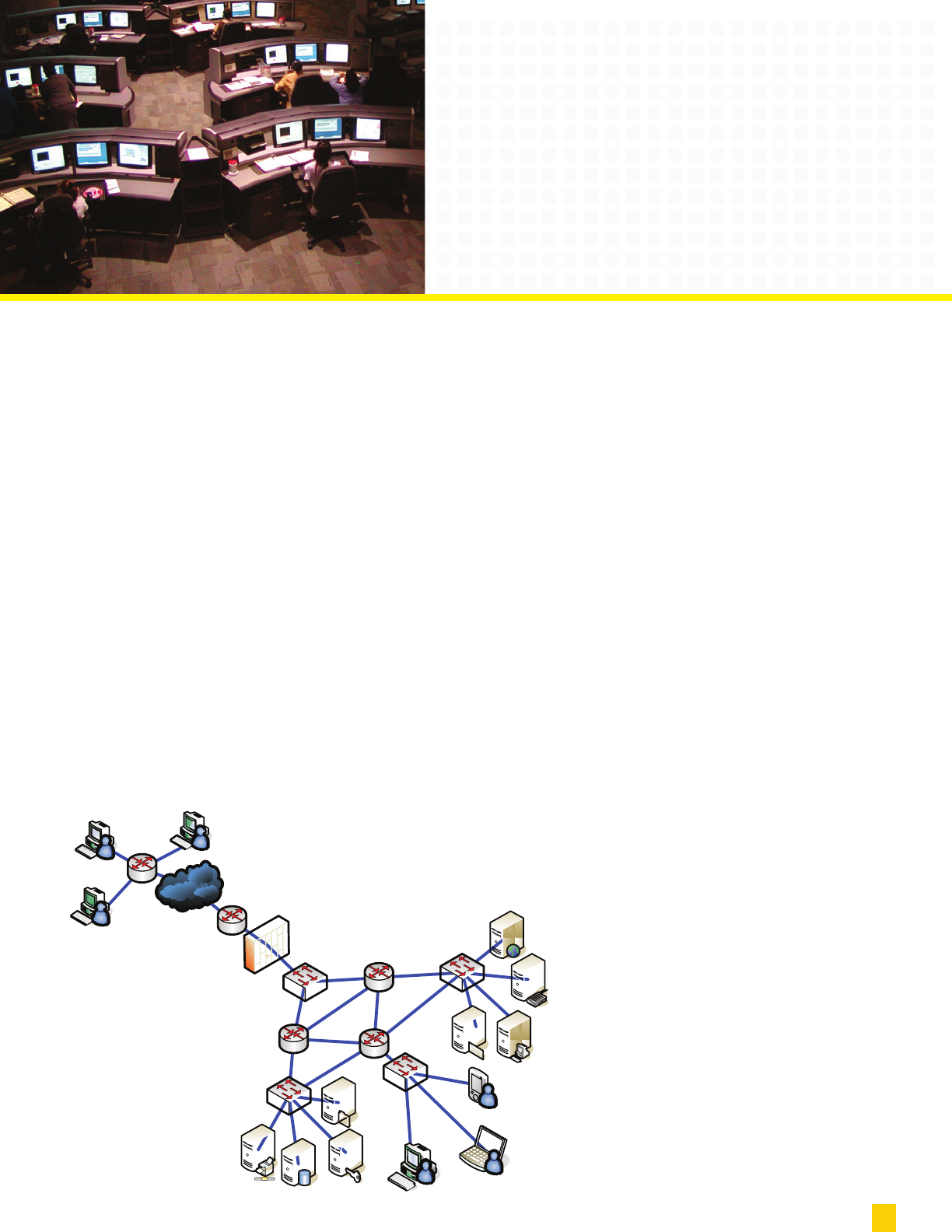
Understanding The Needs
Of Your Business
Proper power protection and
environmental control is essential
for your network components:
■
Printer servers
■
Database servers
■
File servers
■
E-mail servers
■
Web servers
■
Routers
■
Hubs
Your Network Has Many Points That
Must Be Protected
Your customers have
expectations of the level
of system availability you
can provide.