PN 82013151
16
Identity Information
5. SSH Sentinel uses certificates and digital signatures as its primary authentication
method. SSH Sentinel processes certificates according to the IETF Public-Key
Infrastructure X.509v3 standards, allowing you to take advantage of the public-key
infrastructure (PKI). SSH Sentinel supports certificate revocation lists (CRLs) and
authority revocation lists (ARLs, that is, CRLs for CAs) and is very configurable.
However, you can run the software as stand-alone, separately from any public-key
infrastructure.
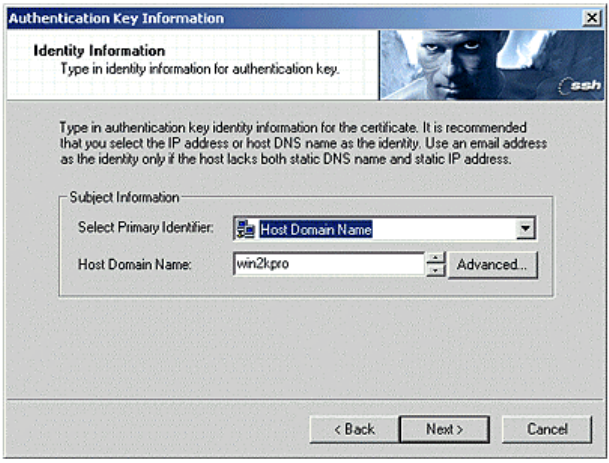
The setup requires host identity information that is to be associated with the
authentication key pair and its certificate. A commonly preferred identity is the host
DNS name, also referred to as the Fully Qualified Domain Name (FQDN). The DNS name
should be used as the identity whenever the host has a static DNS name and whenever
it is safe to assume that name service will be available. If the host does not have a
static DNS name, its static IP address may be used as the host identity.
If neither static DNS name nor IP address is available, you may use an email address as
the identity. However, using an email address as the identity makes it difficult for
remote hosts to bind IPSec rules for the host, since rules are normally bound to a host
name or an IP address.
Figure 7. Inquiring Certificate Identity.


















