Security 8-71
your network may be vulnerable.
AA
AA
nn
nn
aa
aa
pp
pp
pp
pp
rr
rr
oo
oo
aa
aa
cc
cc
hh
hh
tt
tt
oo
oo
uu
uu
ss
ss
ii
ii
nn
nn
gg
gg
ff
ff
ii
ii
ll
ll
tt
tt
ee
ee
rr
rr
ss
ss
The ultimate goal of network security is to prevent unauthorized access to the network without compromising
authorized access. Using filter sets is part of reaching that goal.
Each filter set you design will be based on one of the following approaches:
■ “That which is not expressly permitted is prohibited.”
■ “That which is not expressly prohibited is permitted.”
The first rule is far more secure, and is the best approach to filter design. It is far easier (and more secure) to
allow in or out only certain services and deny anything else. If the other rule is used, you would have to figure
out everything that you want to disallow, now and in the future.
FF
FF
ii
ii
ll
ll
tt
tt
ee
ee
rr
rr
ii
ii
nn
nn
gg
gg
tt
tt
uu
uu
tt
tt
oo
oo
rr
rr
ii
ii
aa
aa
ll
ll
GG
GG
ee
ee
nn
nn
ee
ee
rr
rr
aa
aa
ll
ll
ff
ff
ii
ii
ll
ll
tt
tt
ee
ee
rr
rr
ii
ii
nn
nn
gg
gg
tt
tt
ee
ee
rr
rr
mm
mm
ss
ss
Filter rule: A filter set is comprised of individual filter rules.
Filter set: A grouping of individual filter rules.
Firewall: A component or set of components that restrict access between a protected network and the Internet,
or between two networks.
Host: A workstation on the network.
Packet: Unit of communication on the Internet.
Packet filter: Packet filters allow or deny packets based on source or destination IP addresses, TCP or UDP
ports, or the TCP ACK bit.
Port: A number that defines a particular type of service.
BB
BB
aa
aa
ss
ss
ii
ii
cc
cc
II
II
PP
PP
pp
pp
aa
aa
cc
cc
kk
kk
ee
ee
tt
tt
cc
cc
oo
oo
mm
mm
pp
pp
oo
oo
nn
nn
ee
ee
nn
nn
tt
tt
ss
ss
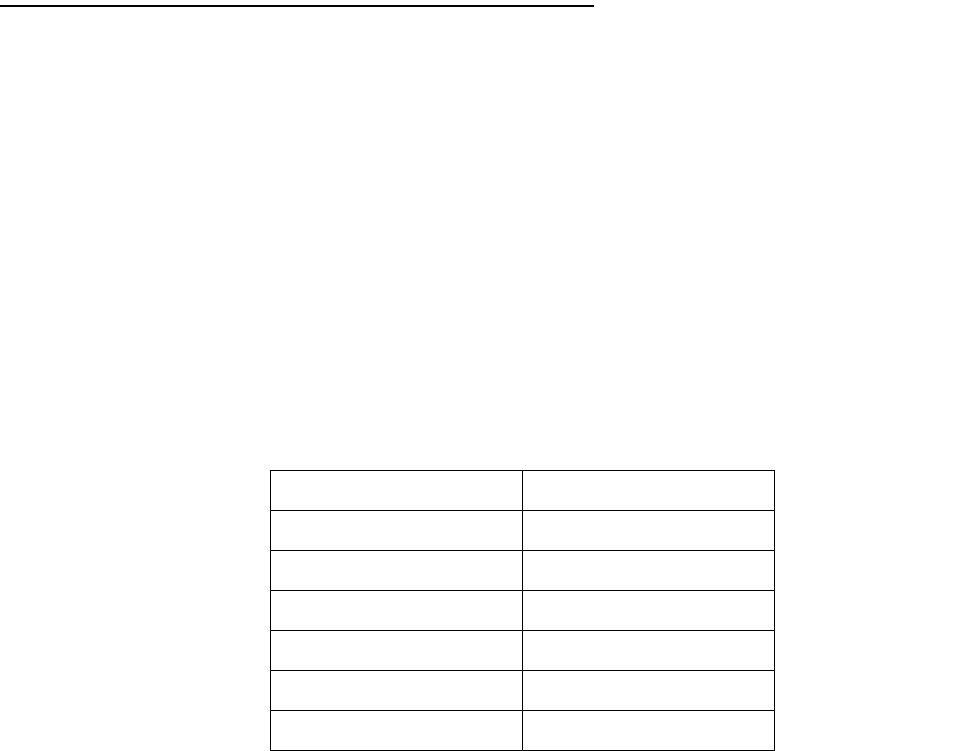
All IP packets contain the same basic header information, as follows:
Source IP Address 163.176.132.18
Destination IP Address 163.176.4.27
Source Port 2541
Destination Port 80
Protocol TCP
ACK Bit Yes
DATA User Data


















