27
The difference between WPA and WPA2 is that WPA2 provides
data encryption via the AES. In contrast, WPA uses Temporal Key
Integrity Protocol (TKIP).
Encryption Method
Security Off – Disable the encryption mode.
WEP – Enable the WEP Data Encryption. When the item is
selected, you have to continue setting the WEP Encryption keys.
TKIP – TKIP (Temporal Key Integrity Protocol) changes the
temporal key every 10,000 packets (a packet is a kind of message
transmitted over a network.) This insures much greater security
than the standard WEP security.
AES – AES has been developed to ensure the highest degree of
security and authenticity for digital information and it is the most
advanced solution defined by IEEE 802.11i for the security in the
wireless network.
Note: All devices in the network should use the same encryption
method to ensure the communication.
802.1x Authentication
Protocol
The EAP authentication protocols this device has supported are
included as follows. This setting has to be consistent with the
wireless APs or Routers that the card intends to connect.
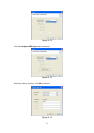
EAP/TLS (User Certificate) –EAP/TLS is the most secure of the
EAP protocols but not easy to use. It requires that digital
certificates be exchanged in the authentication phase. The server
presents a certificate to the client. After validating the server’s
certificate, the client presents a client certificate to the server for
validation.
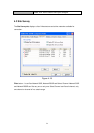
Passphrase
The WPA-PSK / WPA2-PSK can be from 8 to 64 characters and
can be letters or numbers. This same key must be used on all of
the wireless stations in the network.
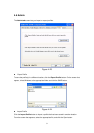
WEP Key(Key1 ~ Key4)
The WEP keys are used to encrypt data transmitted in the wireless
network. There are two types of key length: 40-Bit and 104-Bit.
Fill the text box by following the rules below.
40-Bit – Input 10-digit Hex values (in the “A-F”, “a-f” and “0-9”
range) or 5-digit ASCII characters (including “a-z” and “0-9”) as the
encryption keys. For example: “0123456aef“ or “test1”.
104-Bit – Input 26-digit Hex values (in the “A-F”, “a-f” and “0-9”
range) or 13-digit ASCII characters (including “a-z” and “0-9”) as
the encryption keys. For example:
“01234567890123456789abcdef“ or “administrator”.