Features
·Batteries
·Toner/Ink Cartridges
·
Electronic Circuit Boards
Authentication
Functions
for an Array of Fields
Components
·Personal Computers/
Office Equipment
·Toys
·
Home Networking Devices
Equipment
·Films/Music
·Game Software
·
Books
Content
·USB Token Key
·Entrance Locks
·
Smart Keys
Consumer
Applications
Application Fields
Authentication Microcomputer Positioning
Security level
High
Low
Product Specifications
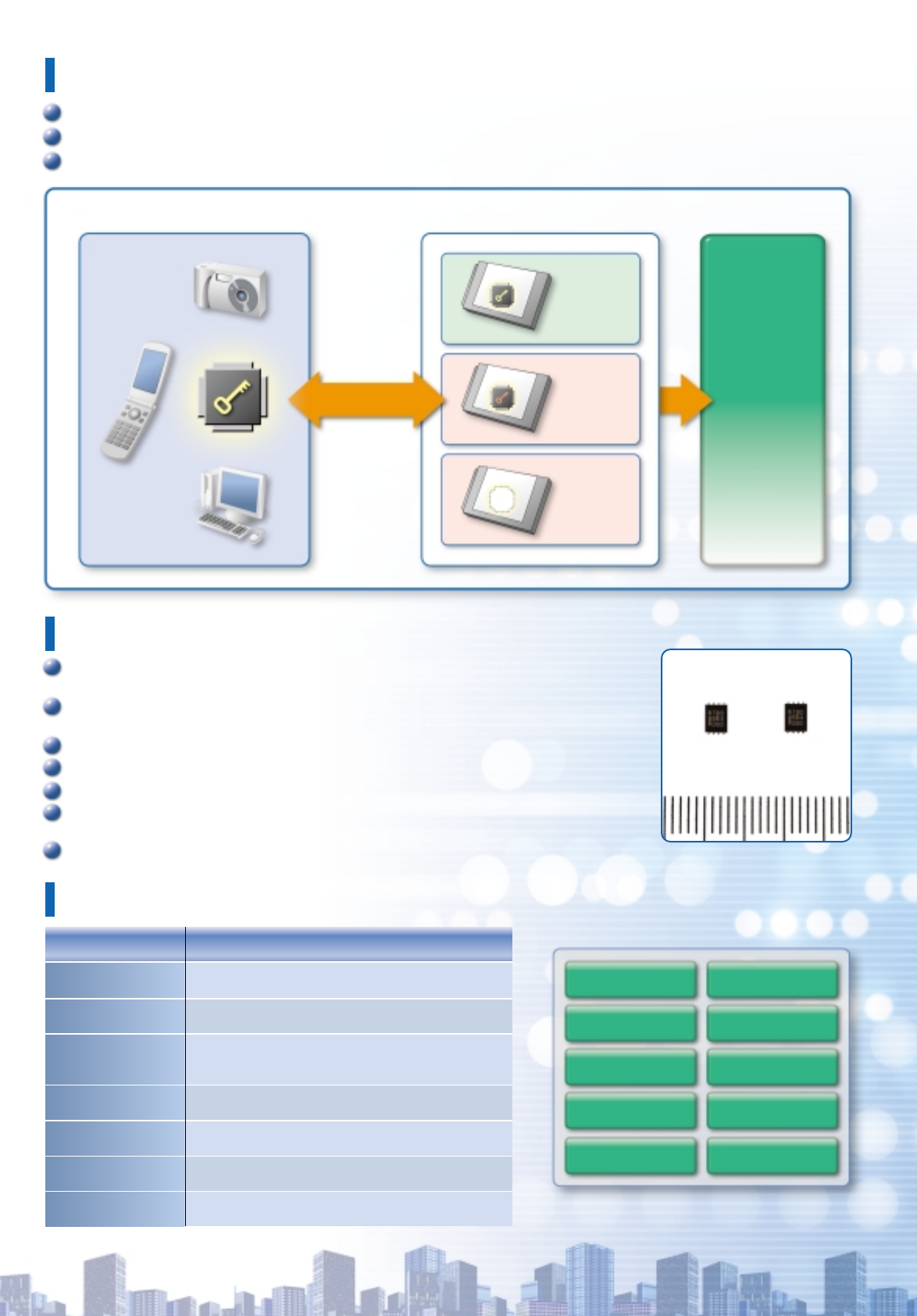
Authentication System Concept
System Components (Key Data)
0101···011
Match
Authentication Microcomputer
No Match
No
Authentication
BATTERY
Authentication Microcomputer
BATTERY
BATTERY
Authentication Microcomputer
Block Diagram
The built-in authentication microcomputer stores the matching key data and accurately transmits the authentication results.
Security is enhanced by encrypting data transfers between the system and individual components.
Unauthorized access is prevented by the strong anti-tampering function incorporated into the authentication microcomputer.
Uses a secure communications protocol to verify the identity of devices attempting to
establish a connection.
Strong anti-tampering function prevents unauthorized access to the authentication
microcomputer.
Fast encryption processing function supports rapid data encryption and decryption.
Built-in EEPROM non-volatile memory for storing data and programs.
Slim security IP core for a compact package.
A variety of encryption libraries (DES, 3DES, and MISTY public key encryption,
etc.)are available.
Support for the development of necessary software.
SSU
H8/300H
CPU
System Control
Logic
ROM
(16KByte)
RAM
(512Byte)
EEPROM
(512Byte)
Clock
generator
Security
Logic
PORT
RNG
R5H30101
H8/300H high-performance 16-bit CPU
Model No.
CPU
*
ReMarkey
TM
is a trademark of Renesas Technology Corp. in Japan.
Item Specification
SSU, RNG, I/O ports, security
DES, 3DES, and MISTY, etc.
2.2~3.6V
WSON-8 (3.00 x 4.06, 0.65 mm pitch)
512 B EEPROM non-volatile memory,
16KB ROM, 512B RAM
Memory
Peripheral functions
Encryption libraries
Power supply voltage
Package
Security Threats What Needs Protecting
·Product Reliability (Safety)
·Personal Information/Copyright
·Corporate Brands
Security Measures
Forgery
Fraud
Data Destruction
Requiring authentication in order to connect makes it possible to verify the reliability of equipment and component
Highly confidential data, such as personal information and product parameters, can be stored in encrypted form.
Anti-tampering functions similar to those used in smart cards can be used to prevent unauthorized deciphering of data.
Elevated Security
In the age of ubiquitous networking, everyone is linked everywhere, all the time.
In a networked society, security threats including forgery, fraud, and data loss are numerous and varied.
Security means limiting access to specific persons, in specific places, at specific times.
RNG:Random Number Generator
SSU:Synchronous Serial Communication Unit
EEPROM:Electrically Erasable and Programmable Read Only Memory
·Equipment and
Component authentication
·Data Encryption
·Digital Watermarks
·Access Control
A key device for establishing corporate brand prestige
ReMarkey
TM
Secure Authentication Microcomputer
Security Level of
Conventional Consumer
Products
Standard MCU
Security Level Necessary
in Age of Ubiquitous Networking
·Safe Network Connections
·Data Protection
·Strong Ability to Defeat Security Attacks
Smart Card Fields
·Financial
·Transportation
·Communications
Encrypted
Data Transfer
Authentication
Results
In the age of ubiquitous networking
security enhances product value
and corporate brand prestige.








