Cruzer Enterprise Product Specifications
Revision 1.0
2.2 Data Security
The Cruzer Enterprise security architecture combines hardware-based access control and security features
that are insulated from the host computer environment.
Cruzer Enterprise implements a double security mechanism, access control and data encryption, based on
SHA-1 and AES algorithms. Encrypted data is stored in a secure zone, hidden until successful authentication
is completed by the Cruzer Enterprise access control mechanism. This method of encryption and
authentication is more secure than software commands. Data is encrypted and decrypted dynamically within
the device, thus only data required by the host PC is decrypted and sent to the PC.
2.2.1 Access Control - Maximum Number of Attempts (Max
NOA)
Cruzer Enterprise locks automatically for further access after a predefined number of consecutive, incorrect
password attempts. This number is defined during the manufacturing process. This feature prevents brute
force attacks, where the hacker tries several password variations in order to determine the correct password.
2.2.2 Encryption Algorithms
Cruzer Enterprise implements industry-standard symmetric and asymmetric algorithms. No proprietary
algorithms are used.
Symmetric Algorithm
Cruzer Enterprise supports the symmetric AES algorithm described in Table 1.
The Parallel AES Coprocessor is used for fast computation of the Advanced Encryption Standard algorithm.
The AES algorithm is described by the FIPS PUB 197 Advanced Encryption Standard.
Table 1: Symmetric Algorithm used by Cruzer Enterprise
Encryption Algorithm Key Length Encryption Mode
AES 256-bit TDEA Electronic Code Book (TECB)
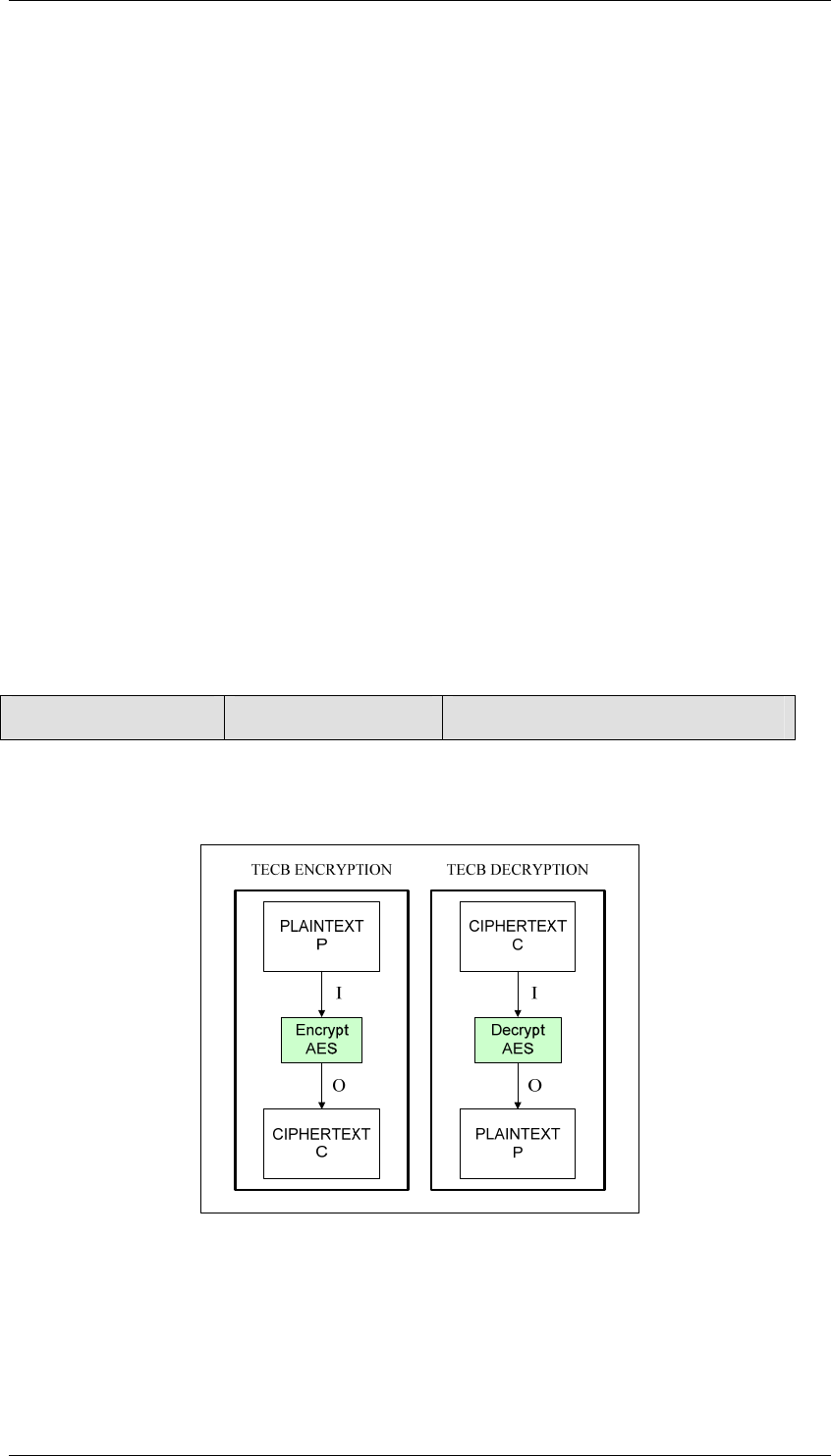
Figure 2 illustrates the encryption flow using the Electronic Code Book (ECB) encryption mode. Details of
the encryption and decryption cycles follow.
Figure 2: TDEA Electronic Code Book (TECB) Mode
In TECB encryption, a 256-bit plaintext data block (P) is used directly as the input block (I). The input block
is processed through the AES encoder using a 256-bit key. The resulting 256-bit output block (O) is used
directly as ciphertext (C).
© 2007 SanDisk® Corporation 4 May, 2007 Document No. PSP-CRE-0507-11












