SEAGATE ENTERPRISE CAPACITY 3.5 HDD V4 SAS PRODUCT MANUAL, REV. A 2
1.0 SCOPE
This manual describes Seagate
®
Enterprise Capacity 3.5 HDD v4 SAS (Serial Attached SCSI) disk drives.
Enterprise Capacity 3.5 HDD v4 drives support the SAS Protocol specifications to the extent described in this manual. The SAS Interface
Manual (part number 100293071) describes the general SAS characteristics of this and other Seagate SAS drives. The Self-Encrypting
Drive Reference Manual, part number 100515636, describes the interface, general operation, and security features available on Self-
Encrypting Drive models.
Product data communicated in this manual is specific only to the model numbers listed in this manual. The data listed in this manual may
not be predictive of future generation specifications or requirements. If designing a system which will use one of the models listed or future
generation products and need further assistance, please contact the Field Applications Engineer (FAE) or our global support services
group as shown in See “Seagate Technology Support Services” on page 1.
Unless otherwise stated, the information in this manual applies to standard and Self-Encrypting Drive models.
.
For more information on FIPS 140-2 Level 2 certification see Section 7.0 on page 37.
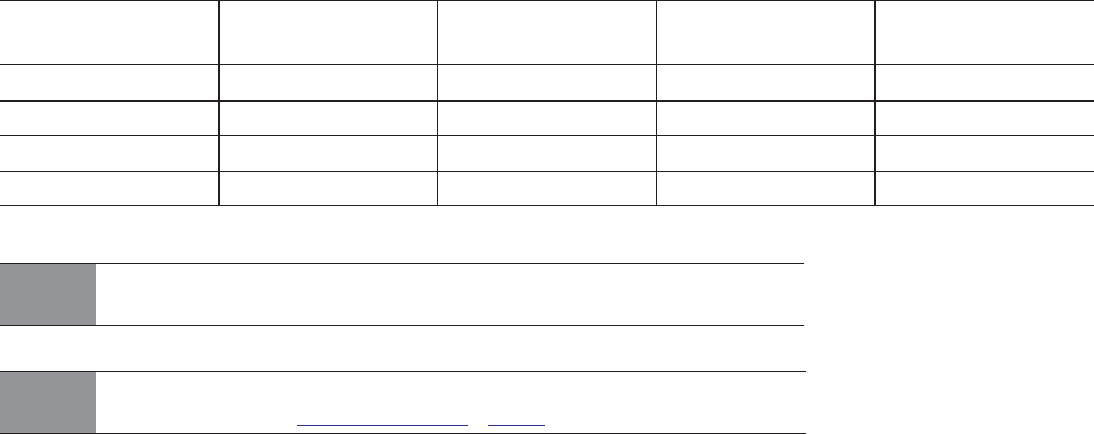
Standard 4KN
models
Standard 5xxE
models
Self-Encrypting
4KN (SED) models
Self-Encrypting
5xxE (SED) models
FIPS 140-2 Level 2
(Review Pending)
ST6000NM0014 ST6000NM0034 ST6000NM0074 ST6000NM0054
4KN model
ST4000NM0014 ST4000NM0034 ST4000NM0074 ST4000NM0054 ST6000NM0114
ST2000NM0014 ST2000NM0034 ST2000NM0074 ST2000NM0054
5xxE model
ST6000NM0104
NOTE
Previous generations of Seagate Self-Encrypting Drive models were called Full Disk
Encryption (FDE) models before a differentiation between drive-based encryption and
other forms of encryption was necessary.
NOTE
The Self-Encrypting Drive models indicated on the cover of this product manual have
provisions for “Security of Data at Rest” based on the standards defined by the Trusted
Computing Group (see www.trustedcomputinggroup.org).


















