XEROX WorkCentre
5735/5740/5745/5755/5765/5775/5790
Information Assurance Disclosure Paper
Ver. 2.00, March 2011 Page 8 of 50
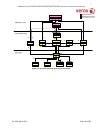
Security Function Subsystem
Security Management
Controller
Graphical User Interface
Table 1 Security Functions allocated to Subsystems
2.2. Controller
2.2.1. Purpose
The controller provides both network and direct-connect external interfaces, and enables copy, print, email, network
scan, server fax, internet FAX, and LanFAX functionality. Network scanning, server fax, internet fax, and LanFax, are
standard features.
NOTE: The Copier only version includes a hard drive which is used to hold Operating System software, printing
applications, and jam clearance videos. Job Image data is not stored on this disk.
Image Overwrite, which is included as a standard feature, enables both Immediate and On-Demand overwrite of any
temporary image data created on disk. The controller also incorporates an open-source web server (Apache) that
exports a Web User Interface (WebUI) through which users can submit jobs and check job and machine status, and
through which system administrators can remotely administer the machine.
The controller contains the image path, which uses proprietary hardware and algorithms to process the scanned
images into high-quality reproductions. Scanned images may be temporarily buffered in DRAM to enable electronic
pre-collation, sometimes referred to as scan-once/print-many. When producing multiple copies of a document, the
scanned image is processed and buffered in the DRAM in a proprietary format. Extended buffer space for very large
documents is provided on the network disk. The buffered bitmaps are then read from DRAM and sent to the Image
Output Terminal (IOT) for marking on hardcopy output. For long documents, the production of hardcopy may begin
before the entire original is scanned, achieving a level of concurrency between the scan and mark operations.
The controller operating system is Wind River Linux, kernel v. 2.6.20+. (Note: Consistent with Flaw Remediation, this
baseline may be updated as indicated by the ‘+’ sign. Unnecessary services such as rsh, telnet and finger are disabled
in the OS. FTP is used in client-only mode by the network scanning feature for the filing of scanned images and the
retrieval of Scan Templates; however the controller does not contain an FTP server.
The controller works with the Graphical User Interface (GUI) assembly to provide system configuration functions. A
System Administrator PIN must be entered at the GUI in order to access these functions.
2.2.2. Memory Components
Volatile Memory
Type (SRAM, DRAM,
etc)
Size
User
Modifiable
(Y/N)
Function or Use
Process to Sanitize
DDR2 SDRAM
Upgradeable to
1GB
2GB
N Single Board Controller
(System and user image stored)
Subsequent jobs overwrite
the data and all images are
lost at power off or reboot.
Additional Information:
There are also a number of RAM buffers in the video path that are used for image
manipulation (Reduce/Enlarge, etc.), and all have no data retention capability. When power is removed all data is lost.
These buffers are typically built into the ASICs. Typical bleed down time for all volatile memory is 10 seconds.