Total: 1700
• vpn-out
• Priority 6: VoIP 500 kpbs
• Priority 0: Best effort
Total: 1700
• in-pipe
• Priority 6: VoIP 500 kpbs
Total: 2000
• out-pipe
• Priority 6: VoIP 500 kpbs
Total: 2000
The following pipe rules are then needed to force traffic into the correct pipes and precedence
levels:
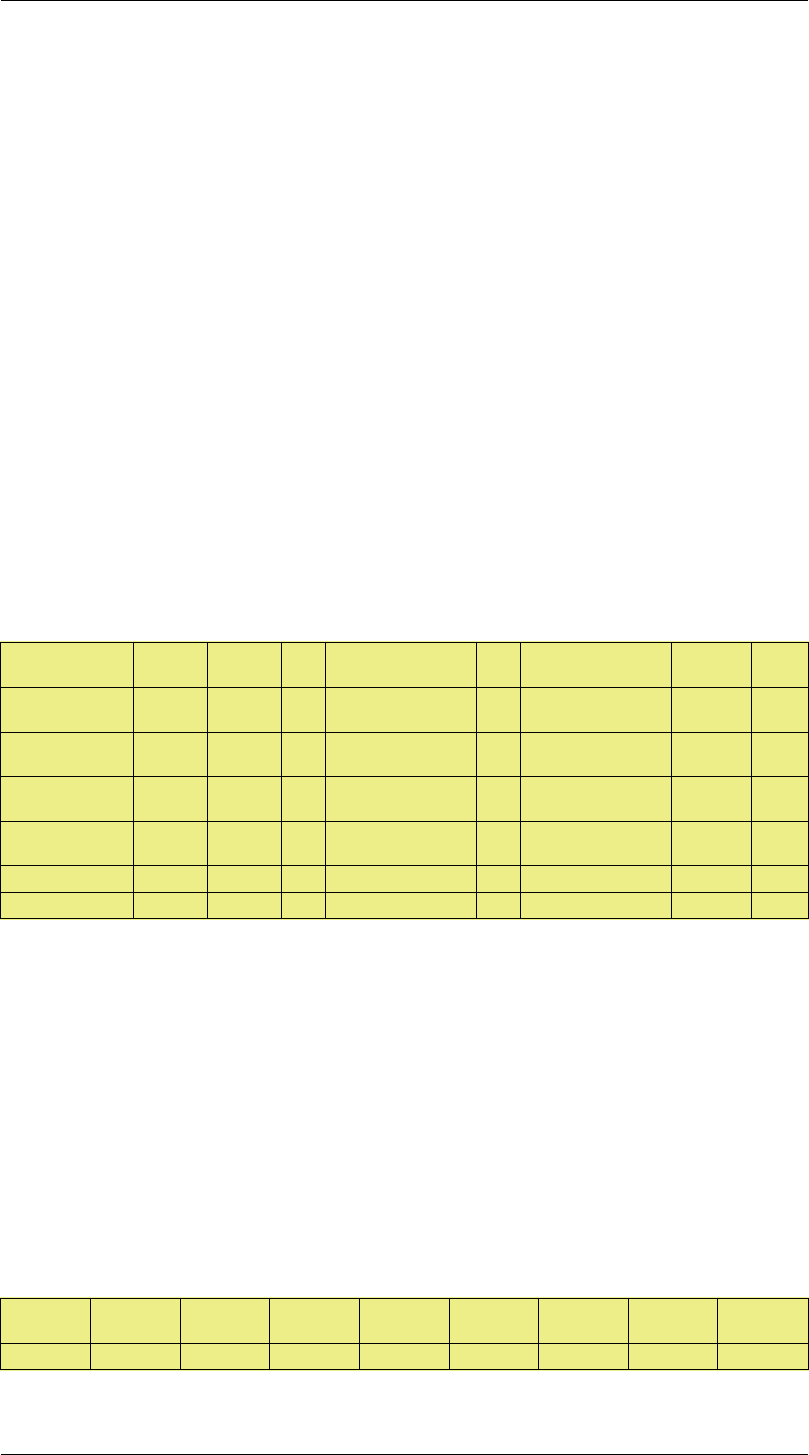
Rule
Name
Forward
Pipes
Return
Pipes
Src
Int
Source
Network
Dest
Int
Destination
Network
Selected
Service
Prece
dence
vpn_voip_out vpn-out
out-pipe
vpn-in
in-pipe
lan lannet vpn vpn_remote_net H323 6
vpn_out vpn-out
out-pipe
vpn-in
in-pipe
lan lannet vpn vpn_remote_net All 0
vpn_voip_in vpn-in
in-pipe
vpn-out
out-pipe
vpn vpn_remote_net lan lannet H323 6
vpn_in vpn-in
in-pipe
vpn-out
out-pipe
vpn vpn_remote_net lan lannet All 0
out out-pipe in-pipe lan lannet wan all-nets All 0
in in-pipe out-pipe wan all-nets lan lannet All 0
With this setup, all VPN traffic is limited to 1700 kbps, the total traffic is limited to 2000 kbps and
VoIP to the remote site is guaranteed 500 kbps of capacity before it is forced to best effort.
SAT with Pipes
If SAT is being used, for example with a web server or ftp server, that traffic also needs to be forced
into pipes or it will escape traffic shaping and ruin the planned quality of service. In addition, server
traffic is initiated from the outside so the order of pipes needs to be reversed: the forward pipe is the
in-pipe and the return pipe is the out-pipe.
A simple solution is to put a "catch-all-inbound" rule at the bottom of the pipe rule. However, the
external interface (wan) should be the source interface to avoid putting into pipes traffic that is
coming from the inside and going to the external IP address. This last rule will therefore be:
Rule
Name
Forward
Pipes
Return
Pipes
Source
Interface
Source
Network
Dest
Interface
Dest
Network
Selected
Service
Prece
dence
all-in in-pipe out-pipe wan all-nets core all-nets All 0
10.1.10. More Pipe Examples Chapter 10. Traffic Management
463
