CHAPTER 2: DRILL DOWN INTO A URL GAUGE STEP 3: VIEW A LIST OF USERS AFFECTING A CHILD GAUGE
6 8E6 TECHNOLOGIES, THREAT ANALYSIS REPORTER EVALUATION GUIDE
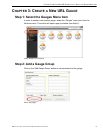
Step 3: View a List of Users Affecting a Child Gauge
Double-click the child gauge to open a window containing a list of users who are
responsible for driving that gauge’s score. In this example, double-click the
“Spyware” child gauge.
Open the child gauges window
Step 4: View an Individual User’s Gauge Activity
In the Spyware window, select the top name from the user list and click “User
Summary” to get a complete view of all activity for that user. This will help deter-
mine if the user is just abusing a single category or has high activity in other
gauges as well.
View a list of end users who are responsible for a gauge’s activity