61
traveling between authorized devices.
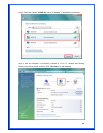
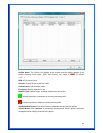
WPA2 – Like WPA, WPA2 supports IEEE 802.1x/EAP authentication or PSK
technology. It also includes a new advanced encryption mechanism using the
Advanced Encryption Standard (AES). AES is required to the corporate user or
government users. The different between WPA and WPA2 is that WPA2 provides
data encryption via the AES. In contrast, WPA uses Temporal Key Integrity
Protocol (TKIP).
WPA2-PSK – WPA2-PSK is also for home and small business. The difference
between WPA-PSK and WPA2-PSK is that WPA2-PSK provides data encryption
via the AES. In contrast, WPA-PSK uses Temporal Key Integrity Protocol (TKIP).
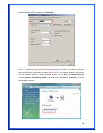
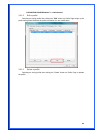
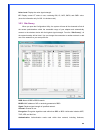
Encryption: The encryption of the desired network.
-- For Open and Shared authentications, the available encryption modes are
None and WEP.
-- For WPA, WPA-PSK, WPA2 and WPA2-PSK authentications, the available
modes are TKIP and AES.
None – Disable the Encryption mode.
WEP – Enabled the WEP Data Encryption. When the item is selected, you have to
continue setting the WEP Key Length & the key Index.
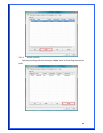
TKIP – TKIP (Temporal Key Integrity Protocol) changes the temporal key every
10000 packets (a packet is a kind of message transmitted over a network). This
insures much greater security than the standard WEP security.
AES – AES has been developed to ensure the highest degree of security and
authenticity for digital information and it is the most advanced solution defined by
IEEE 802.11i for the security in the wireless network.
Note: All devices in the network should use the same encryption method to ensure
the communication.
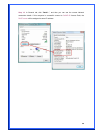
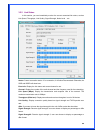
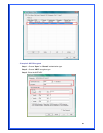
WPA Pre-Shared Key: The WPA-PSK key can be from 8 to 64 characters and can
be letters or numbers. This same key must be used on all of the wireless stations in
the network.
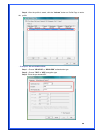
WEP Key (Key1~Key4): The WEP keys are used to encrypt data transmitted in the
wireless network. There are two types of key length: 64-bit & 128-bit. Select the
default encryption key form key1 to key4 by selected the radio button.
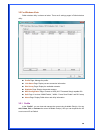
Fill the text box by following the rule below:
64-bit – Input 10-digit Hex values (in the “A-F”, “a-f, and “0-9” range) or 5-digit
ASCII characters (including “a-z” and “0-9”) as the encryption keys. For example:
“0123456aef” or “test1”
128-bit – Input 26-digit Hex values (in the “A-F”, “a-f, and “0-9” range) or 13-digit
ASCII characters (including “a-z” and “0-9”) as the encryption keys. For example: