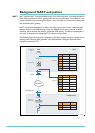
Headquarters
Page 11 | AlliedWare™ OS How To Note: VPNs for Corporate Networks
Check that you have a 3DES feature licence for the ISAKMP policies.
show feature
You can purchase feature licences from your Allied Telesis distributor.
If necessary, install the licence, using the password provided by your distributor.
enable feature=3des pass=<licence-number>
Enable IPsec
enable ipsec
In this example, IPsec SA specifications propose:
z ISAKMP as the key management protocol
z ESP as the IPsec protocol
z (for site-to-site VPNs) 3DESOUTER as the encryption algorithm for ESP
z (for site-to-site VPNs) SHA as the hashing algorithm for ESP authentication
z (for roaming client VPNs) four possible variants of VPN encryption, for added flexibility.
We propose the most secure option first.
Create an SA specification for the branch office site-to-site VPN. This SA specification uses
tunnel mode by default.
create ipsec sas=1 key=isakmp prot=esp enc=3desouter hasha=sha
Create a group of SA specifications for the roaming VPN clients. These SA specifications use
IPsec transport mode for Windows VPN interoperability. Multiple specifications allow IPsec
to negotiate different levels of encryption to match what your version of the VPN client
provides.
create ipsec sas=2 key=isakmp prot=esp enc=3desouter hasha=sha
mod=transport
create ipsec sas=3 key=isakmp prot=esp enc=3desouter hasha=md5
mod=transport
create ipsec sas=4 key=isakmp prot=esp enc=des hasha=sha mod=transport
create ipsec sas=5 key=isakmp prot=esp enc=des hasha=md5 mod=transport
Create two IPsec bundles, one for the remote branch routers and one for the roaming VPN
clients.
create ipsec bund=1 key=isakmp string="1"
create ipsec bund=2 key=isakmp string="2 or 3 or 4 or 5"
6. Check feature licences
7. Configure the VPNs for the branch offices and roaming clients