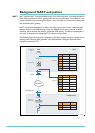
Headquarters
Page 12 | AlliedWare™ OS How To Note: VPNs for Corporate Networks
Create IPsec policies to bypass IPsec for ISAKMP messages and the “port floated” key
exchange that NAT-T uses.
create ipsec pol=isakmp int=eth0 ac=permit lp=500 rp=500
create ipsec pol=isakmp_float int=eth0 ac=permit lp=4500
Create an IPsec policy for the VPN traffic between headquarters and branch office
1
. Identify
the traffic by its local and remote addresses—in this example the subnet used on the LAN at
branch office
1
(remote) is
1
92.
1
68.
1
4
1
.0/24. Note that the local address selector is wider
than the headquarter’s LAN; in fact, we cover all site subnets with this supernet.
create ipsec pol=branch1 int=eth0 ac=ipsec key=isakmp isa=branch1
bund=1 peer=222.222.222.1 lad=192.168.0.0 lma=255.255.0.0
rad=192.168.141.0 rma=255.255.255.0
Create another IPsec policy for the VPN traffic between headquarters and branch office 2.
The subnet used on the LAN at branch office 2 is
1
92.
1
68.
1
42.0/24. This policy uses
peeraddress=dynamic. The dynamic option is designed for only one dynamic peer to
connect at a time under that policy, which makes sense when the policy is intended for one
branch office.
create ipsec pol=branch2 int=eth0 ac=ipsec key=isakmp isa=branch2
bund=1 peer=dynamic lad=192.168.0.0 lma=255.255.0.0
rad=192.168.142.0 rma=255.255.255.0
Create another IPsec policy for roaming VPN clients to access headquarters. Identify the
traffic by the L2TP port (UDP traffic to port
1
70
1
). This policy uses peeraddress=any. The
any option allows simultaneous VPN clients to be set up under the policy.
create ipsec pol=roaming int=eth0 ac=ipsec key=isakmp bund=2 peer=any
isa=roaming lp=1701 tra=udp
Create another IPsec policy for direct Internet traffic from the headquarters LAN to the
Internet, such as web browsing.
create ipsec pol=internet int=eth0 ac=permit
Note: The order of the IPsec policies is important. The Internet permit policy must be last.
Create your ISAKMP pre-shared key. This key is used when initiating your VPN during phase
one ISAKMP exchanges with your VPN peers. Share the value of this pre-shared key with all
VPN peers that use it—in this example, the roaming VPN clients and the branch office
routers. The router only uses this key during phase one ISAKMP exchanges.
create enco key=1 type=general value=<alphanumeric-preshared-key>
Enable ISAKMP.
ena isa
This example uses separate ISAKMP policies for each peer. Note the following points about
the policies:
z different ISAKMP policies meet the different needs of the different types of peer—Allied
Telesis routers versus Windows VPN clients. For example, Allied Telesis peers support
heartbeats; Windows VPN clients do not.