ENGLISH
42
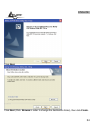
Authentication and Security
This function is used to protect wireless communication from eavesdropping. A
secondary function of encryption is to prevent unauthorized access to a wireless
network, and it can be achieved by using the Encryption function. This Adapter
provides only WEP security when used in Access Point mode.
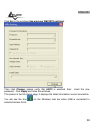
• Fragmentation Threshold: To set the number of bytes used for the
fragmentation boundary for directed messages. Default is 2340 bytes.
• RTS Threshold: To set the size of RTS/CTS packet size. Default is 2340 bytes.
• Preamble: Preamble frames. Long preamble (128 bits sync field) and short
preamble (56 bits sync field) are supported. System default is long preamble.
• Mac Address Filter: AP connected or can’t connect with Mac address that user
setting.
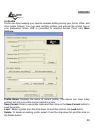
Filter
Type
Reject Access Disable
Result
Access Control
function doesn’t
allows clients whose
MAC addresses in the
list will be able to
connect to this
Access Point.
Access Control
function allows clients
whose MAC
addresses in the list
will be able to connect
to this Access Point.
Access Point
doesn’t check MAC
addresses
• Bridge Adapter: Select the device where you want the wireless packets to be
sent to.
The range of radio frequencies used by IEEE 802.11g wireless devices
is called a “channel”. Channels available depend on your geographical
area. You may have a choice of channels (for your region) so you should
use a different channel than an adjacent AP (access point) to reduce
interference. Interference occurs when radio signals from different
access points overlap causing interference and degrading performance.
Adjacent channels partially overlap however. To avoid interference due
to overlap, your AP should be on a channel at least five channels away
from a channel that an adjacent AP is using. For example, if your region
has 11 channels and an adjacent AP is using channel 1, then you need
to select a channel between 6 or 11.