Billion BIPAC-8500 / 8520 SHDSL VPN Firewall Bridge / Router
Chapter 4: Configuration
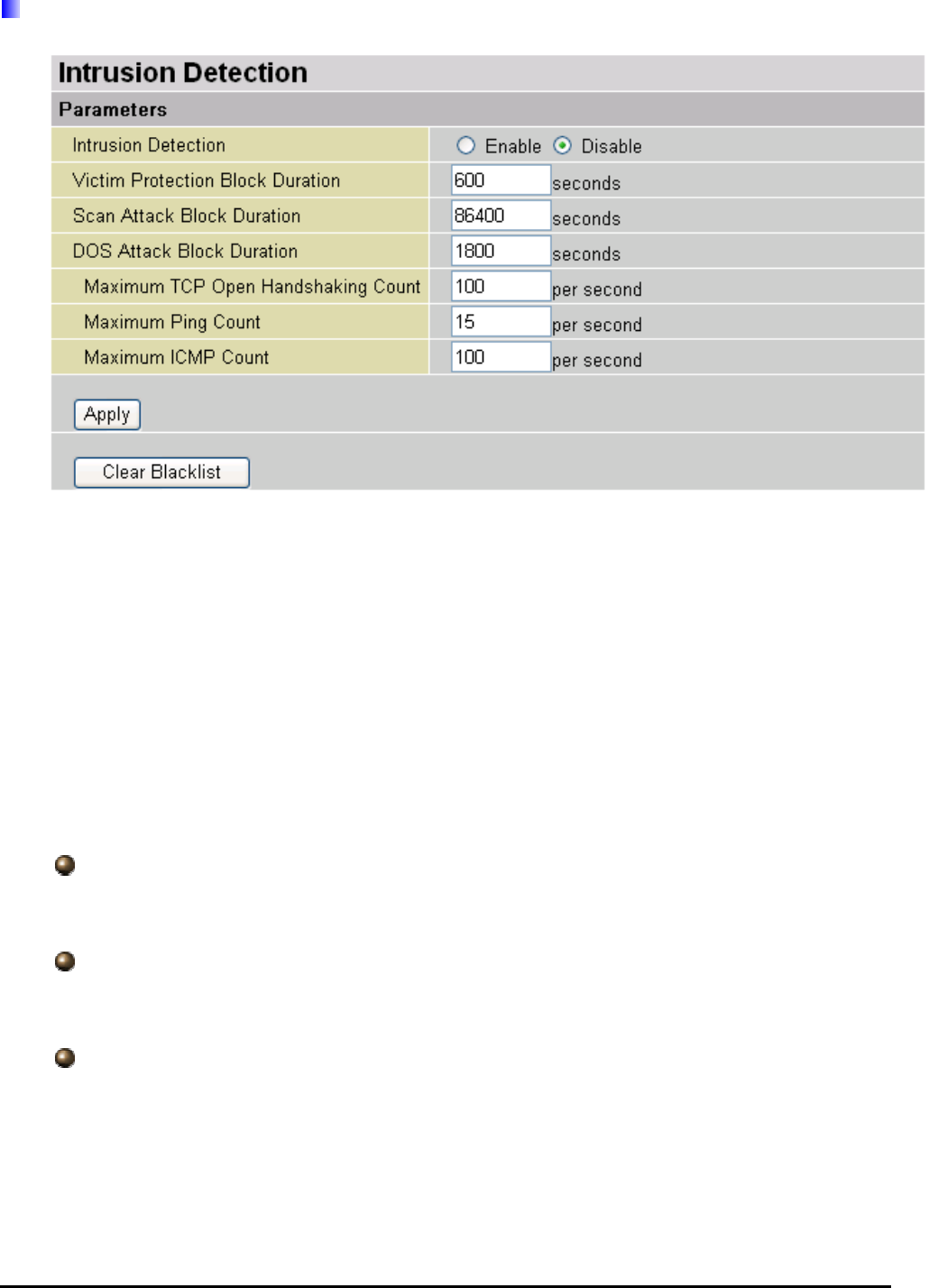
Intrusion Detection
The router’s Intrusion Detection System (IDS) is used to detect hacker attacks and
intrusion attempts from the Internet. If the IDS function of the firewall is enabled, inbound
packets are filtered and blocked depending on whether they are detected as possible
hacker attacks, intrusion attempts or other connections that the router determines to be
suspicious.
Blacklist: If the router detects a possible attack, the source IP or destination IP address
will be added to the Blacklist. Any further attempts using this IP address will be blocked for
the time period specified as the Block Duration. The default setting for this function is
false (disabled). Some attack types are denied immediately without using the Blacklist
function, such as Land attack and Echo/CharGen scan.
Block Duration:
DoS Attack Block Duration: This is the duration for blocking hosts that attempt a
possible Denial of Service (DoS) attack. Possible DoS attacks this attempts to block
include Ascend Kill and WinNuke. Default value is 1800 seconds.
Scan Attack Block Duration: This is the duration for blocking hosts that attempt a
possible Scan attack. Scan attack types include X’mas scan, IMAP SYN/FIN scan
and similar attempts. Default value is 86400 seconds.
Victim Protection Block Duration: This is the duration for blocking Smurf attacks.
Default value is 600 seconds.
Victim Protection: If enabled, IDS will block Smurf attack attempts. Default is false.
Max TCP Open Handshaking Count: This is a threshold value to decide whether a SYN
Flood attempt is occurring or not. Default value is 100 TCP SYN per seconds.
60


















