2-2
WLSE Express AAA Server Certificate Configuration Guide
OL-8880-01
Chapter 2 Generating Certificates
Generating Certificates with OpenSSL
The CR usually contains the following:
• An RSA key-pair
• Subject name (possibly in DN format)
• Desired lifetime of the certificate
• Name or identification of the issuing (signing) CA
• Certificate extensions
PEAP and EAP-TLS require server certificates to include an extendedKeyUsage extension of TLS Server
Authentication and client certificates to include an extendedKeyUsage extension of TLS Client
Authentication. The method used to specify extensions and their values depends on the tool. The
extendedKeyUsage extension contains one or more Object Identifier (OID) values which are specified
as strings of dot-separated decimals. The appropriate values are shown below:
Certificate Generation
The CR is submitted to the CA to generate the actual certificate. This might happen immediately, upon
request (such as using a web form) or there might be delays if the CA is operated offline or requires
manual management approval to issue certificates.
Generating Certificates with OpenSSL
This section provides example of creating certificates with OpenSSL. The OpenSSL open source project
includes a command line tool, openssl, used to create keys and certificates. OpenSSL has many other
useful capabilities. For more information about the OpenSSL open source project, check their website:
http://www.openssl.org
The examples create an extremely simple certificate hierarchy consisting of two levels and three
certificates. First a self-signed root certificate is created and then used to sign a server certificate and a
client certificate. Most realistic certificate hierarchies contain one or more levels of intermediate CA
certificates.
The following steps assume a Linux or BSD-style shell is active, but the commands for most other
command line environments are similar.
The openssl.cnf Configuration File
The openssl command tool uses a configuration file usually named openssl.cnf for various parameters
and other information related to creating certificate requests.
There are two ways to make the openssl.cnf file available to the command tool:
• Using the OPENSSL_CONF environment variable
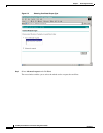
Table 2-1 Required Values of extendedKeyUsage
Server or Client OID Value Meaning
Server 1.3.6.1.5.5.7.3.1 TLS Server Authentication
Client 1.3.6.1.5.5.7.3.2 TLS Client Authentication