2-6
WLSE Express AAA Server Certificate Configuration Guide
OL-8880-01
Chapter 2 Generating Certificates
Certificate Generation with Windows CA
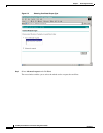
Use the following command to display the server certificate:
openssl x509 –in ./ca/certs/client-cert.pem –text
Converting a Client Certificate and Private Key to PKCS#12
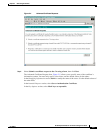
Use the following command sequence to convert a client certificate and private key to PKCS#12. This
process is useful for importing a client certificate to a Windows PC for testing.
cat ./ca/certs/client-cert.pem ./ca/private/client-key.pem > ./ca/private/client-all.pem
openssl pkcs12 –export –in client-all.pem –out client-all.p12
Certificate Generation with Windows CA
This section provides examples of creating certificates using the Windows Certificate Authority
(Windows CA). The Windows CA provides a web-based interface for requesting and retrieving
certificates. The web forms permit you to create a new key pair or use an existing key, specify the desired
certificate fields and attributes, and to submit the request to the CA for processing.
Note The Windows CA component is only available on Windows Server OS, not on client OS (such as
Windows 2000 Pro or Windows XP). To generate certificates you will need a Windows Server set up and
the Windows CA configured.
Usually an administrator will be required to manually review and grant or deny the request before the
certificate can be accessed. (Windows CA can also be configured to automatically grant requests without
administrator intervention.) The Certification Authority snap-in of the Microsoft Management Console
(MMC) is used to review certificate requests and take the appropriate action. It can also be used for other
purposes such as certificate revocation, renewal, etc.
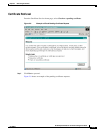
After a certificate has been issued by the Windows CA it must be exported to a file so that it can be
transported to the machine where it will be used. Although Windows can export certificates in DER or
PEM format, if the corresponding private key is required (as it is for server and client certificates) then
the certificate and private key will be bundled into a PKCS#12-formatted file. Since the required format
for our purposes is PEM, the PKCS#12 content must be reformatted appropriately.
The following examples show an extremely simple certificate hierarchy consisting of two levels and
three certificates. Most realistic certificate hierarchies will contain one or more levels of intermediate
CA certificates. Since the root-level certificate is created when the Windows CA product is installed and
configured, those steps are not shown here. The examples assume that the Windows CA has been
configured for standalone operation, but the steps are essentially the same for other configurations.
The following examples assume that the Windows Certificate Authority product has been installed and
configured. Since the exact installation steps vary depending on the version of Windows Certificate
Authority and its configuration, those steps are not shown here. Refer to the appropriate Microsoft
documentation for information about how to install Windows Certificate Authority.