Configuring RADIUS Server Support for Switch Services
Configuring and Using RADIUS-Assigned Access Control Lists
Displaying the Current RADIUS-Assigned ACL Activity
on the Switch
These commands output data indicating the current ACL activity imposed per-
port by RADIUS server responses to client authentication.
Syntax: show access-list radius < port-list >
For the specified ports, this command lists the explicit ACEs, switch
port, and client MAC address for each ACL dynamically assigned by
a RADIUS server as a response to client authentication. If cnt
(counter) is included in an ACE, then the output includes the current
number of inbound packet matches the switch has detected in the
current session for that ACE.
Note: If a client authenticates but the server does not return a
RADIUS-assigned ACL to the client port, then the server does not have
a valid ACL configured and assigned to that client’s authentication
credentials.
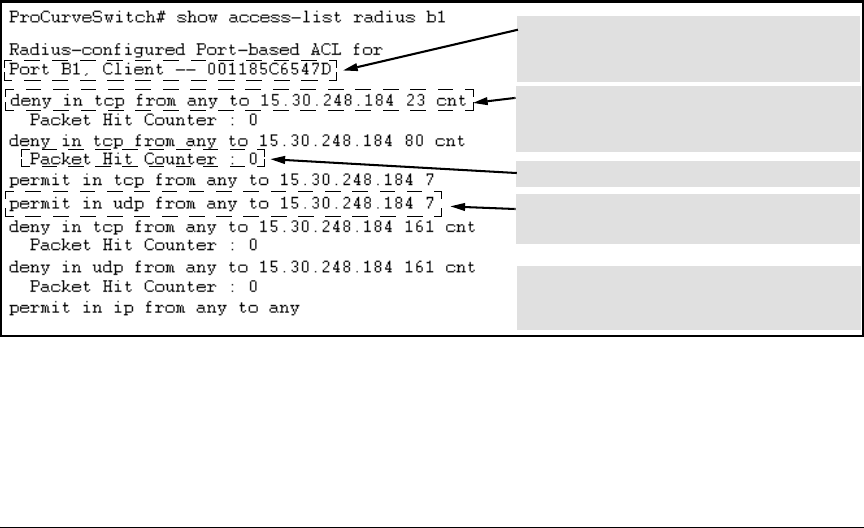
For example, the following output shows that a RADIUS server has assigned
an ACL to port B1 to filter inbound traffic from an authenticated client
identified by a MAC address of 00-11-85-C6-54-7D.
Indicates MAC address identity of the authenticated
client on the specified port. This data identifies the
client to which the ACL applies.
Lists “deny” ACE for Inbound Telnet (23 = TCP port
number) traffic, with counter configured to show the
number of matches detected.
Lists current counter for the preceding “Deny” ACE.
Lists “permit” ACEs for inbound TCP and UDP traffic,
with no counters configured.
Note that the implicit “deny any/any” included
automatically at the end of every ACL is not visible in
ACL listings generate by the switch.
Figure 6-7. Example Showing a RADIUS-assigned ACL Application to a Currently Active Client Session
6-26


















