14
White Paper: The All New 2010 Intel® Core™ vPro™ Processor Family: Intelligence that Adapts to Your Needs
Filter threats and isolate PCs
automatically based on IT policy
Laptop and desktop PCs with a new Intel Core vPro processor include
programmable filters that monitor inbound and outbound network
traffic for threats. IT managers can use third-party software to define
the policies that will trigger hardware-based isolation of a PC.
Both laptops and desktop PCs with a new Intel Core vPro processor use
programmable, hardware-based filters for examining packet headers
for suspicious behavior. Desktop PCs also include additional hardware-
based filters that monitor the rate of outbound traffic to help identify
suspicious behavior, including both fast-moving and slow-moving
worms.
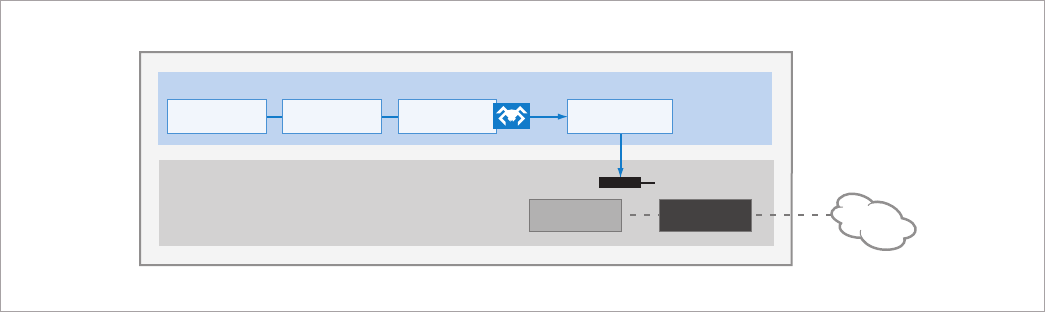
Both laptop and desktop PCs also include built-in isolation circuitry
(see Figure 4). When a threat is identified, a policy and hardware-based
“switch” can:
• Isolate the system by specific port(s) to halt a suspicious type of
traffic.
• Disconnect the network data path to the OS (the remediation port
remains open) to contain threats more quickly.
• Rate-limit network traffic to give a technician more time to investi-
gate a threat.
During a quarantine, the isolation circuitry disconnects the PC’s
network communication via hardware/firmware at the software stack
in the OS. This is a more secure disconnect than traditional software-
based isolation, which can be circumvented by hackers, viruses, worms,
and user tampering.
Automated, continual checking for agents
Traditionally, IT organizations have used serial polling to verify the pres-
ence of security agents (or other business-critical applications). Because
this method can saturate the network with healthy heartbeats (restrict-
ing the bandwidth available for productive traffic), IT organizations often
poll for compliance only once or twice a day – if that often.
In contrast, laptop and desktop PCs with a new Intel Core vPro processor
use a regular, programmable “heartbeat” presence check, which is built
into the Intel® Management Engine. The heartbeat uses a “watchdog”
timer so third-party software can check in with the Intel Management
Engine at programmable intervals, to confirm that the agent is still
active. Each time an agent checks in, it resets its timer. If an agent hasn’t
checked in before the timer goes off, the agent is presumed removed,
tampered with, or disabled. The Intel Management Engine then auto-
matically and immediately logs the alert and notifies (if specified) the
IT console.
With hardware-based heartbeats, IT administrators no longer need
to wait for multiple polls to identify a potential problem. The PC itself
helps improve the reliability of presence checks and reduce the window
of software vulnerability. And, these “healthy” heartbeats never
leave the PC. Only when there is a problem is an alert sent across the
network, so your network isn’t flooded with healthy heartbeat signals,
and you still receive rapid notification of problems. For wireless laptops,
agent presence checking is enabled even when operating outside
the corporate network through a host OS-based VPN. This gives IT
administrators greater visibility of these highly mobile and traditionally
unsecured assets.
Combined with the remote power-up capability, the entire process
of checking and reinstalling missing agents can also be automated,
improving compliance further and saving additional resources.
Internet
PC hardware
User OS
Intel® AMT Isolation
OS network stack
User ApplicationUser ApplicationUser Application
Hardware-based
filters
Hardware
network stack
Figure 4. System defense filters inspect network traffic. A PC with a new Intel® Core™ vPro™ processor can port-isolate itself or cut off its own
network data path to quarantine itself when suspicious behavior is recognized even if its OS is not available to help prevent threats from spreading
to the network.


















