How ICEcap Manager Works With RealSecure Desktop Protector
15
locally installed. Silent Desktop Protector installations are always completely ICEcap-
controlled. For more information about silent agent installations, see the RealSecure ICEcap
Manager User Guide.
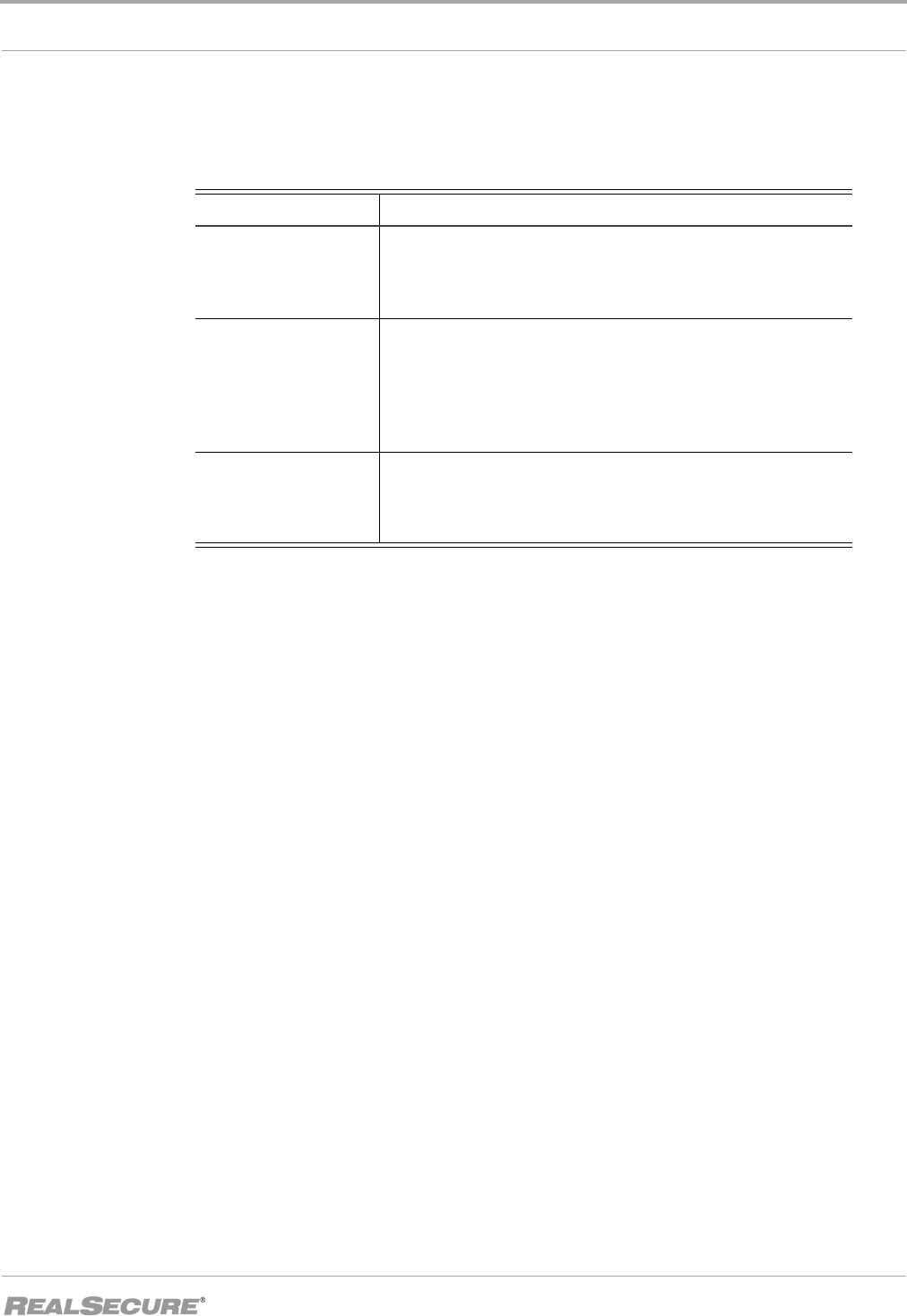
This table summarizes the levels of control ICEcap Manager can exert over an agent.
What level of
control is in effect?
The ICEcap control level determines what you can do with the firewall and Application
Protection components of Desktop Protector on your computer.
To see what level of control ICEcap Manager has over Desktop Protector on your
computer:
1. From the Main Menu, select To ol s
ÆEdit BlackICE Settings.
2. Is the Enable local configuration editing checkbox visible?
■ If yes, you have some degree of control over Desktop Protector on your system.
■ If no, ICEcap Manager has total control of the agent on your system.
3. Which option is selected under Configuration Priority?
■ Remote: the local agent is under shared ICEcap Control. You can alter any
parameters that ICEcap Manager has not explicitly set.
■ Local: the agent is under shared local control. You can override any parameters
ICEcap Manager has set.
Control Level Result
Total ICEcap Control ICEcap Manager has complete control over these agents. If the
local host has the Local Console installed, the end user can
modify the display and alarm preferences but not the blackice.ini
or firewall.ini files. Configuration settings are disabled.
Shared ICEcap Control The local system has partial control over configuration settings,
and can alter any parameters that ICEcap Manager has not
explicitly set. For example, the user can trust an address that
ICEcap Manager does not trust. However, the user cannot
unblock an ICEcap-blocked address or change the protection
level ICEcap Manager enforces.
Shared Local Control The local system has control over all configuration settings.
Although ICEcap Manager distributes configuration settings to
all agents in the group, the end user can override any of those
configuration settings.
Table 8: Levels of local or remote control of the local agent


















