C
ONFIGURING
THE
W
IRELESS
B
ARRICADE
4-31
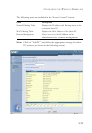
By using the above inspected information and timeout/threshold critieria,
the Wireless Barricade provides the following DoS attack preventions:
Ping of Death (Ping flood) attack, SYN flood attack, IP fragment attack
(Teardrop Attack), Brute-force attack, Land Attack, IP Spoofing attack, IP
with zero length, TCP null scan (Port Scan Attack), UDP port loopback,
Snork Attack etc..
Note: The firewall does not significantly affect system performance, so
we advise enabling the prevention features to protect your network
users.
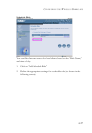
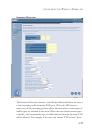
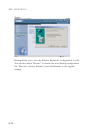
• When hackers attempt to enter your network, we can alert you by e-mail
Enter your E-mail address for alerting hacker access.
Specify your E-mail servers, user name and password.
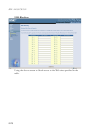
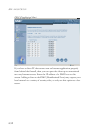
• Connection Policy
Enter the appropriate values for TCP/UDP sessions
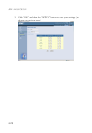
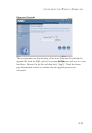
• DoS Criteria and Port Scan Criteria
Setup DoS and port scan criteria in the spaces provided.