53
English
Acer Trusted Platform Module (TPM)
With the development of TCG (Trusted Computing Group, http://
www.trustedcomputinggroup.org/) the Acer Trusted Platform Module offers
the cryptographic implementations of RSA and hash algorithms (SHA-1 and
MD-5) for highest possible performance, as well as a true random number
generator (TRNG).
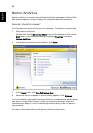
The Acer Security Platform Solution Software is a comprehensive set of tools
that takes advantage of the Trusted Platform Module embedded in your
system. This solution provides services to easily create digital certificates using
the Trusted Platform Module and to manage these certificates.
You can use the certificates to:
• Send and receive secure e-mail from e-mail clients like Microsoft Outlook
Express, Microsoft Outlook or Netscape Messenger
• Set up browser (e.g. Netscape Navigator or Internet Explorer) and web
server (e.g. Microsoft Internet Information Server) for Client
Authentication
• Sign Microsoft Word macros.
• Encrypt files and folders
• Secure network connections
User roles
Security Platform Solution involves several user roles:
All Security Platform user roles are based on Windows user accounts (local or
domain users). These user accounts have been authenticated by Windows
logon.
Each user role has an intended purpose.
When the Security Platform is configured, members of different user roles are
initialized.
Acting a specific user role requires a specific authentication (e.g. providing a
specific password).
A person can act multiple user roles.
The following table lists all user roles.
User Roles:
User Role Based on...
Purpose &
Tasks
Initialization Authentication
Security Platform
Owner
Windows user
account (local or
domain),
member of the
Administrators
group
Perform critical
administrative
tasks, e.g.
restoration of
Security
Platform.
Security Platform
Initialization
enables a Windows
user to act as a
Security Platform
Owner.
Owner Password