56
English
Installation and Administration of Enhanced Authentication
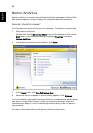
Authentication devices are provided by separately installable software plug-ins.
The Security Platform Solution Software detects installed authentication devices
automatically.
The configuration of authentication devices is user-specific, i.e. different
Security Platform Users can use different authentication devices. Usage of
Enhanced Authentication can be controlled by policies.
Migrating Keys to other Systems
Once a system user is set up as an Acer Security Platform User, there may arise
the requirement to provide the user-specific security environment not only on
the computer where the setup happened, but also on other computers the user
has access to.
Migration Basics
The Acer Security Platform offers the possibility to maintain and administrate
this situation by offering a migration path for the user-specific secret. The basic
idea of this technology is the strict separation of the administrative and
operational role of migration.
The migration operation is performed using the Acer Security Platform
Migration Wizard.
• Migration to a computer without existing user keys and certificates:
The migration process will install new user keys and certificates on the
machine you are migrating to.
You will need to configure Security Platform Features for use with these
new keys and certificates.
• Migration to a computer with existing user keys and certificates (different
Basic User Key):
The migration process will invalidate your existing Security Platform keys
and certificates installed on the machine you are migrating to. Your
encrypted data may be lost as a result of this operation. Please decrypt
your encrypted data before proceeding with migration or contact your
system administrator for data recovery procedure.
• Migration to a computer with existing user keys and certificates (same
Basic User Key):
If the destination computer already uses the same Basic User Key as the
source computer, then the migration process will merge your user keys and
certificates. After migration, the keys and certificates from the migration
archive will be active. Old keys and certificates will be kept. This way you
will not lose any encrypted data.