63D-Link DIR-835 User Manual
Section 3 - Conguration
SPI (Stateful Packet Inspection, also known as dynamic packet ltering)
helps to prevent cyber attacks by tracking more state per session. It
validates that the trac passing through the session conforms to the
protocol.
Select one of the following for TCP and UDP ports:
Endpoint Independent - Any incoming trac sent to an open port
will be forwarded to the application that opened the port. The port
will close if idle for 5 minutes.
Address Restricted - Incoming trac must match the IP address of
the outgoing connection.
Address + Port Restriction - Incoming trac must match the IP address
and port of the outgoing connection.
Enable this feature to protect your network from certain kinds of
“spoong” attacks.
If an application has trouble working from behind the router, you can
expose one computer to the Internet and run the application on that
computer.
Note: Placing a computer in the DMZ may expose that computer to a
variety of security risks. Use of this option is only recommended as a last
resort.
Specify the IP address of the computer on the LAN that you want to have unrestricted Internet communication. If this computer
obtains it’s IP address automatically using DHCP, be sure to make a static reservation on the Setup > Network Settings page so
that the IP address of the DMZ machine does not change.
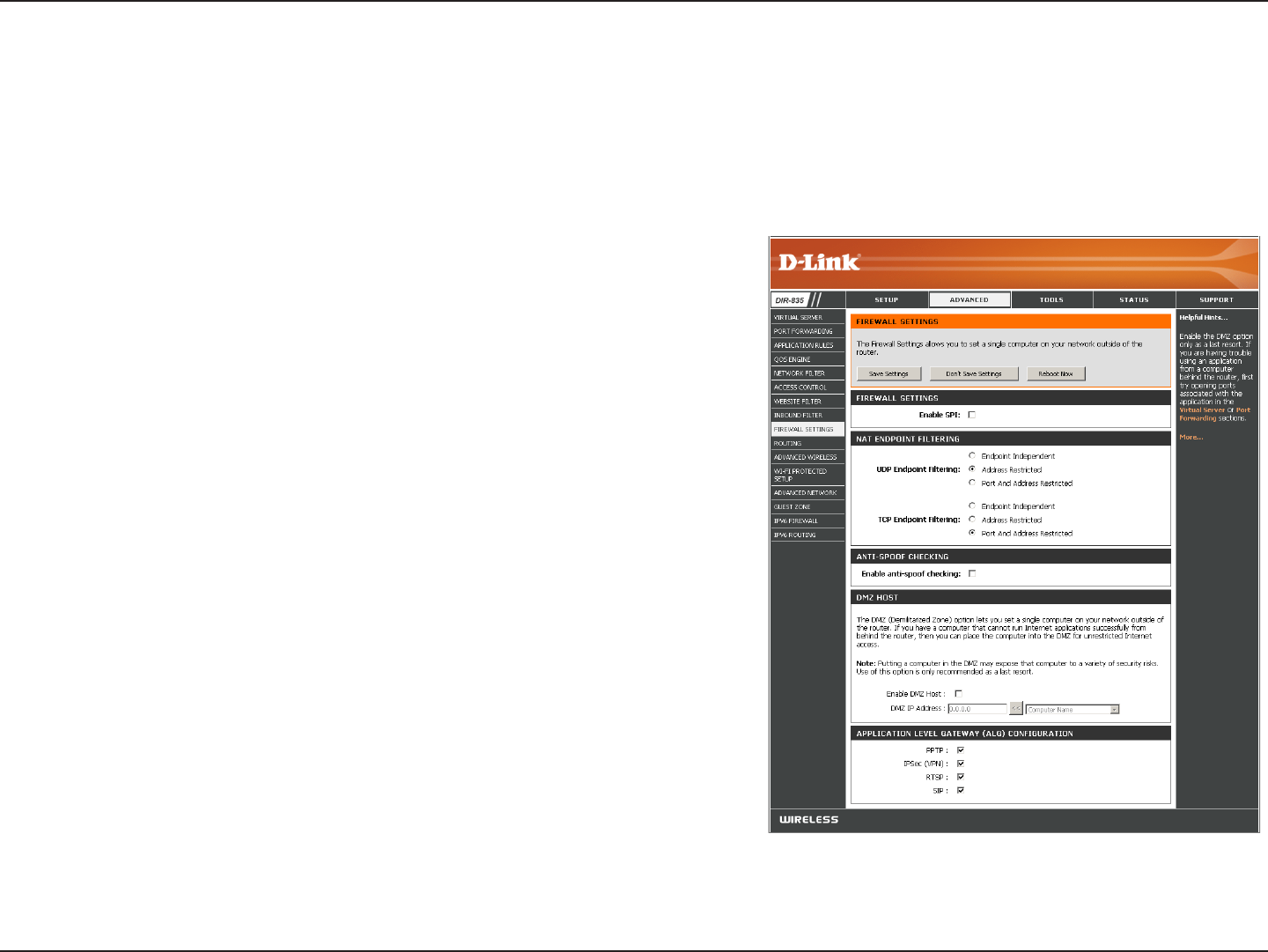
Enable SPI:
NAT Endpoint
Filtering:
Anti-Spoof Check:
Enable DMZ:
DMZ IP Address:
Firewall Settings
A rewall protects your network from the outside world. The DIR-835 oers a rewall type functionality. The SPI feature helps
prevent cyber attacks. Sometimes you may want a computer exposed to the outside world for certain types of applications.
If you choose to expose a computer, you can enable DMZ. DMZ is short for Demilitarized Zone. This option will expose the
chosen computer completely to the outside world.


















