9-30
Configuring and Monitoring Port Security
Reading Intrusion Alerts and Resetting Alert Flags
• In the menu interface:
– The Port Status screen includes a per-port intrusion alert
– The Event Log includes per-port entries for security viola-
tions
• In the web browser interface:
– The Alert Log’s Status | Overview window includes entries for
per-port security violations
– The Intrusion Log in the Security | Intrusion Log window lists
per-port security violation entries
• In an active network management environment via an SNMP trap
sent to a network management station
How the Intrusion Log Operates
When the switch detects an intrusion attempt on a port, it enters a record of
this event in the Intrusion Log. No further intrusion attempts on that port will
appear in the Log until you acknowledge the earlier intrusion event by reset-
ting the alert flag.
The Intrusion Log lists the 20 most recently detected security violation
attempts, regardless of whether the alert flags for these attempts have been
reset. This gives you a history of past intrusion attempts. Thus, for example,
if there is an intrusion alert for port A1 and the Intrusion Log shows two or
more entries for port 1, only the most recent entry has not been acknowledged
(by resetting the alert flag). The other entries give you a history of past
intrusions detected on port A1.
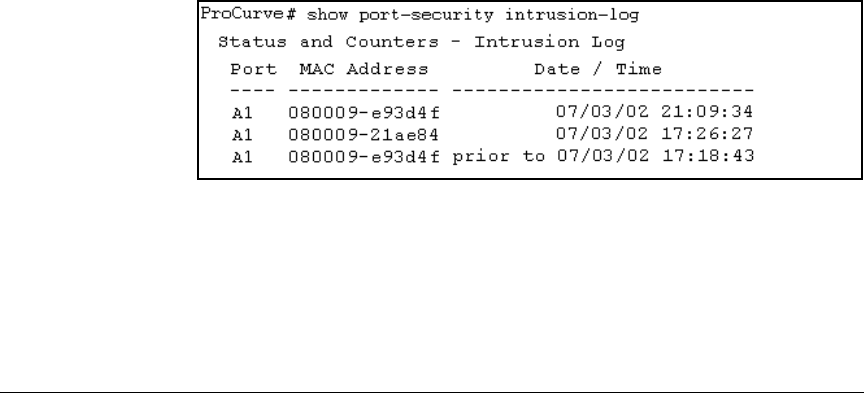
Figure 9-13. Example of Multiple Intrusion Log Entries for the Same Port
The log shows the most recent intrusion at the top of the listing. You cannot
delete Intrusion Log entries (unless you reset the switch to its factory-default
configuration). Instead, if the log is filled when the switch detects a new
intrusion, the oldest entry is dropped off the listing and the newest entry
appears at the top of the listing.


















