8
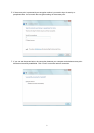
E. If the access point is protected by an encryption method, you need to input its security or
passphrase here. It must match the encryption setting on the access point.
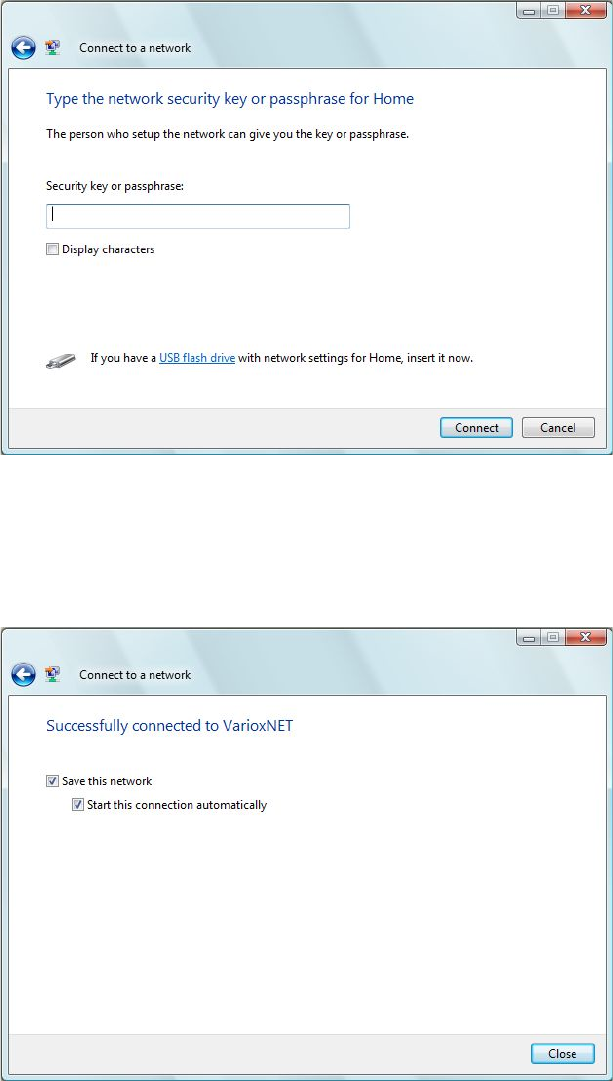
F. If you can see the screen below, the connection between your computer and wireless access point
has been successfully established. Click “Close” to start the network connection.