Chapter 2
Configuration
9
SubProduct
Key Management
Select Auto (IKE) or Manual from the drop-down menu.
The two methods are described below.
Auto (IKE)
Select Auto (IKE) and enter a series of numbers or letters
in the Pre-shared Key field. Based on this word, which
MUST be entered at both ends of the tunnel if this method
is used, a key is generated to scramble (encrypt) the data
being transmitted over the tunnel, where it is unscrambled
(decrypted). You may use any combination of up to 24
numbers or letters in this field. No special characters or
spaces are allowed. In the Key Lifetime field, you may select
to have the key expire at the end of a time period. Enter
the number of seconds you’d like the key to be useful, or
leave it blank for the key to last indefinitely. Check the box
next to PFS (Perfect Forward Secrecy) to ensure that the
initial key exchange and IKE proposals are secure.
Manual
Select Manual, then select the Encryption Algorithm
from the drop-down menu. Enter the Encryption Key in
the field (if you chose DES for your Encryption Algorithm,
enter 16 hexadecimal characters, if you chose 3DES, enter
48 hexadecimal characters). Select the Authentication
Algorithm from the drop-down menu. Enter the
Authentication Key in the field (if you chose MD5 for
your Authentication Algorithm, enter 32 hexadecimal
characters, if you chose SHA1, enter 40 hexadecimal
characters). Enter the Inbound and Outbound SPIs in the
respective fields.
Manual Key Management
Status
The status of the connection is shown.
Click Connect to connect your VPN tunnel. Click View
Logs to view system, UPnP, VPN, firewall, access, or all logs.
Click Advanced Settings and the Advanced IPSec VPN
Tunnel Setup screen will appear.
System Log
When you have finished making changes to the
Security > VPN screen, click Save Settings to save the
changes, or click Cancel Changes to undo your changes.
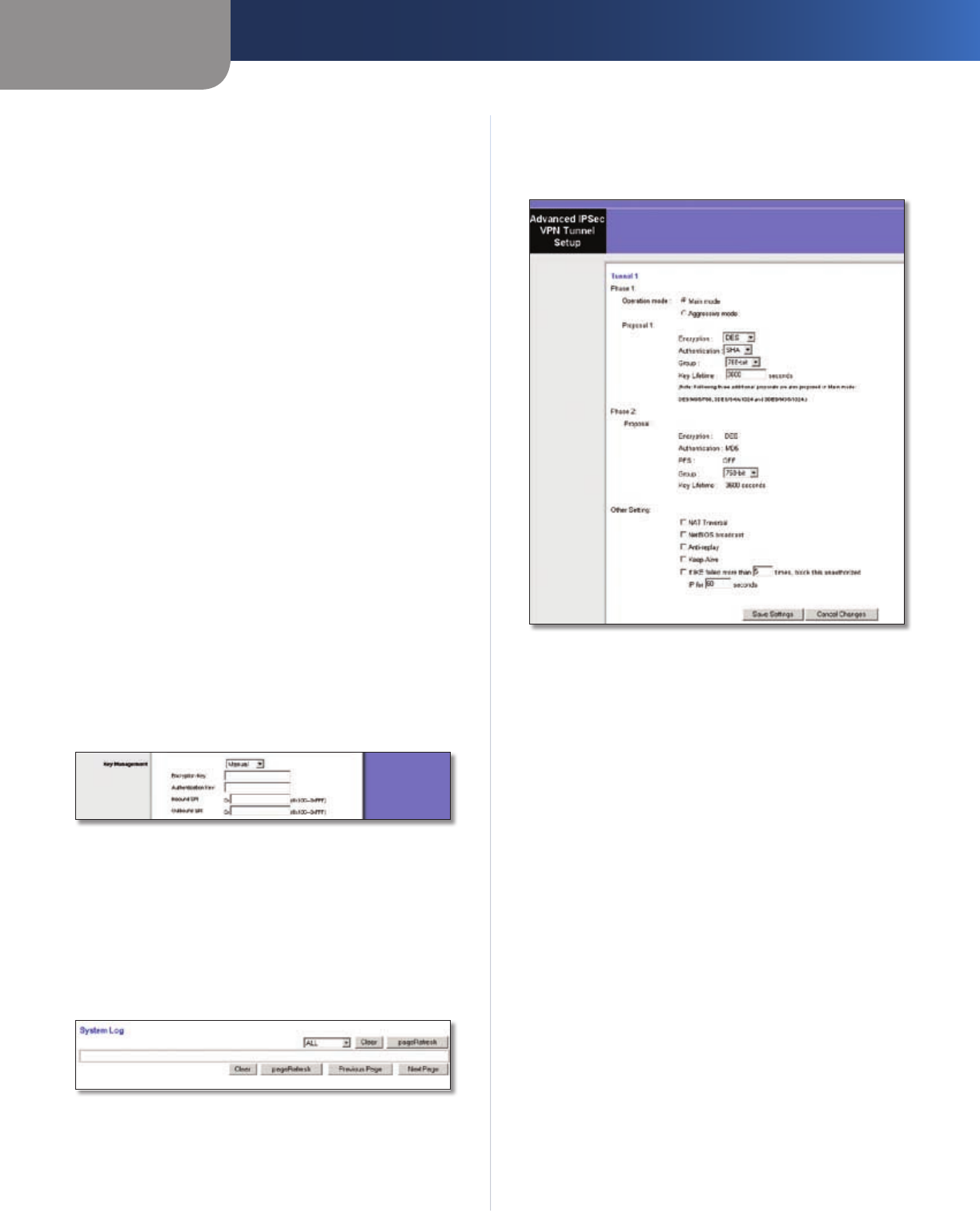
Advanced VPN Tunnel Setup
From the Advanced IPSec VPN Tunnel Setup screen you can
adjust the settings for specific VPN tunnels.
Advanced VPN Tunnel Setup
Phase 1
Phase 1 is used to create a security association (SA), often
called the IKE SA. After Phase 1 is completed, Phase 2 is
used to create one or more IPSec SAs, which are then used
to key IPSec sessions.
Operation Mode There are two modes: Main and
Aggressive, and they exchange the same IKE payloads
in different sequences. Main mode is more common;
however, some people prefer Aggressive mode because
it is faster. Main mode is for normal usage and includes
more authentication requirements than Aggressive mode.
Main mode is recommended because it is more secure.
No matter which mode is selected, the VPN Gateway
will accept both Main and Aggressive requests from the
remote VPN device.
Encryption Select the length of the key used to encrypt/
decrypt ESP packets. There are two choices: DES and 3DES.
3DES is recommended because it is more secure.
Authentication Select the method used to authenticate
ESP packets. There are two choices: MD5 and SHA. SHA is
recommended because it is more secure.
Group There are two Diffie-Hellman Groups to choose
from: 768-bit and 1024-bit. Diffie-Hellman refers to a
cryptographic technique that uses public and private keys
for encryption and decryption.


















