EDS-726 Series User’s Manual Featured Functions
3-51
Authenticator: Edge switch or wireless access point that acts as a proxy between the supplicant
and the authentication server, requesting identity information from the supplicant, verifying the
information with the authentication server, and relaying a response to the supplicant.
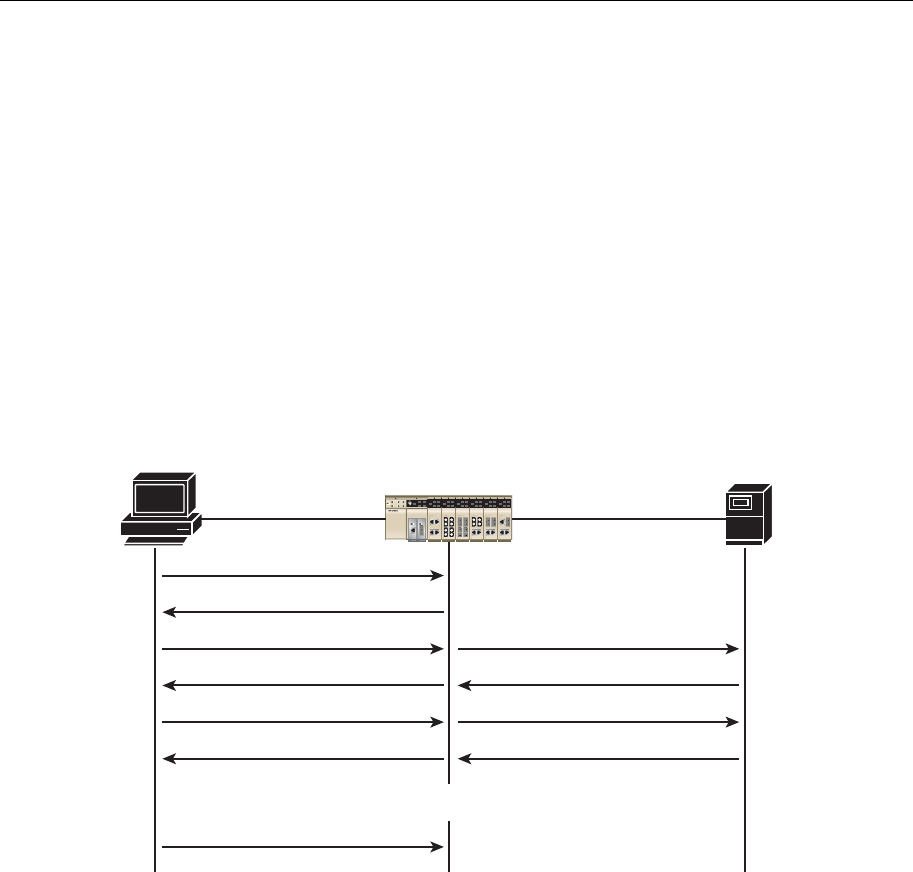
EDS-726 acts as an authenticator in the 802.1X environment. A supplicant and an authenticator
exchange EAPOL (Extensible Authentication Protocol over LAN) frames with each other. We can
either use an external RADIUS server as the authentication server, or implement the authentication
server in EDS-726 by using a Local User Database as the authentication look-up table. When we
use an external RADIUS server as the authentication server, the authenticator and the
authentication server exchange EAP frames between each other.
Authentication can be initiated either by the supplicant or the authenticator. When the supplicant
initiates the authentication process, it sends an “EAPOL-Start” frame to the authenticator. When
the authenticator initiates the authentication process or when it receives an “EAPOL Start” frame,
it sends an “EAP Request/Identity” frame to ask for the username of the supplicant. The following
actions are described below:
Message Exchange
Authentication
server
(RADIUS)
Client
EAPOL-Start
EAP-Request/Identity
EAP-Response/Identity
EAP-Request/OTP
EAP-Response/OTP
EAP-Success
EAPOL-Logoff
Port Authorized
Port Unauthorized
RADIUS Access-Request
RADIUS Access-Challenge
RADIUS Access-Request
RADIUS Access-Accept
EDS-726
EtherDevice Switch
34
IM-4TX
12
PWR
P3
P1
P4
P2
IM-4MST
TX
RX
3 4
TX
RX
1 2
PWR
P3
P1
P4
P2
IM-4MSC
TX
RX
3 4
TX
RX
1 2
PWR
P3
P1
P4
P2
IM-2MST/2TX
TX
RX
3 4
12
PWR
P3
P1
P4
P2
IM-2MSC/2TX
TX
RX
3 4
12
PWR
P3
P1
P4
P2
IM-1LSC/3TX
4
12
3
TX
RX
PWR
P3
P1
P4
P2
COUPLERCF
STAT
PWR1 FAULT
MASTER
PWR2
IM-1GSXSCIM-1GTX
MODE
RING
PORT
COUPLER
PORT
FDX/HDX
LNK/ACT
SPEED
1. When the supplicant receives an “EAP Request/Identity” frame, it sends an “EAP
Response/Identity” frame with its username back to the authenticator.
2. If the RADIUS server is used as the authentication server, the authenticator relays the “EAP
Response/Identity” frame from the supplicant by encapsulating it into a “RADIUS
Access-Request” frame and sends to the RADIUS server. When the authentication server
receives the frame, it looks up its database to check if the username exists. If the username is
not present, the authentication server replies with a “RADIUS Access-Reject” frame to the
authenticator if the server is a RADIUS server or just indicates failure to the authenticator if
the Local User Database is used. The authenticator sends an “EAP-Failure” frame to the
supplicant.
3. The RADIUS server sends a “RADIUS Access-Challenge,” which contains an “EAP Request”
with an authentication type to the authenticator to ask for the password from the client. RFC
2284 defines several EAP authentication types, such as “MD5-Challenge,” “One-Time
Password,” and “Generic Token Card.” Currently, only “MD5-Challenge” is supported. If the
Local User Database is used, this step is skipped.


















