EDS-726 Series User’s Manual Featured Functions
3-52
4. The authenticator sends an “EAP Request/MD5-Challenge” frame to the supplicant. If the
RADIUS server is used, the “EAP Request/MD5-Challenge” frame is retrieved directly from
the “RADIUS Access-Challenge” frame.
5. The supplicant responds to the “EAP Request/MD5-Challenge” by sending an “EAP
Response/MD5-Challenge” frame that encapsulates the user’s password using the MD5 hash
algorithm.
6. If the RADIUS server is used as the authentication server, the authenticator relays the “EAP
Response/MD5-Challenge” frame from the supplicant by encapsulating it into a “RADIUS
Access-Request” frame along with a “Shared Secret,” which must be the same within the
authenticator and the RADIUS server, and sends the frame to the RADIUS server. The
RADIUS server checks against the password with its database, and replies with “RADIUS
Access-Accept” or “RADIUS Access-Reject” to the authenticator. If the Local User Database
is used, the password is checked against its database and indicates success or failure to the
authenticator.
7. The authenticator sends “EAP Success” or “EAP Failure” by the received indication from the
authentication server.
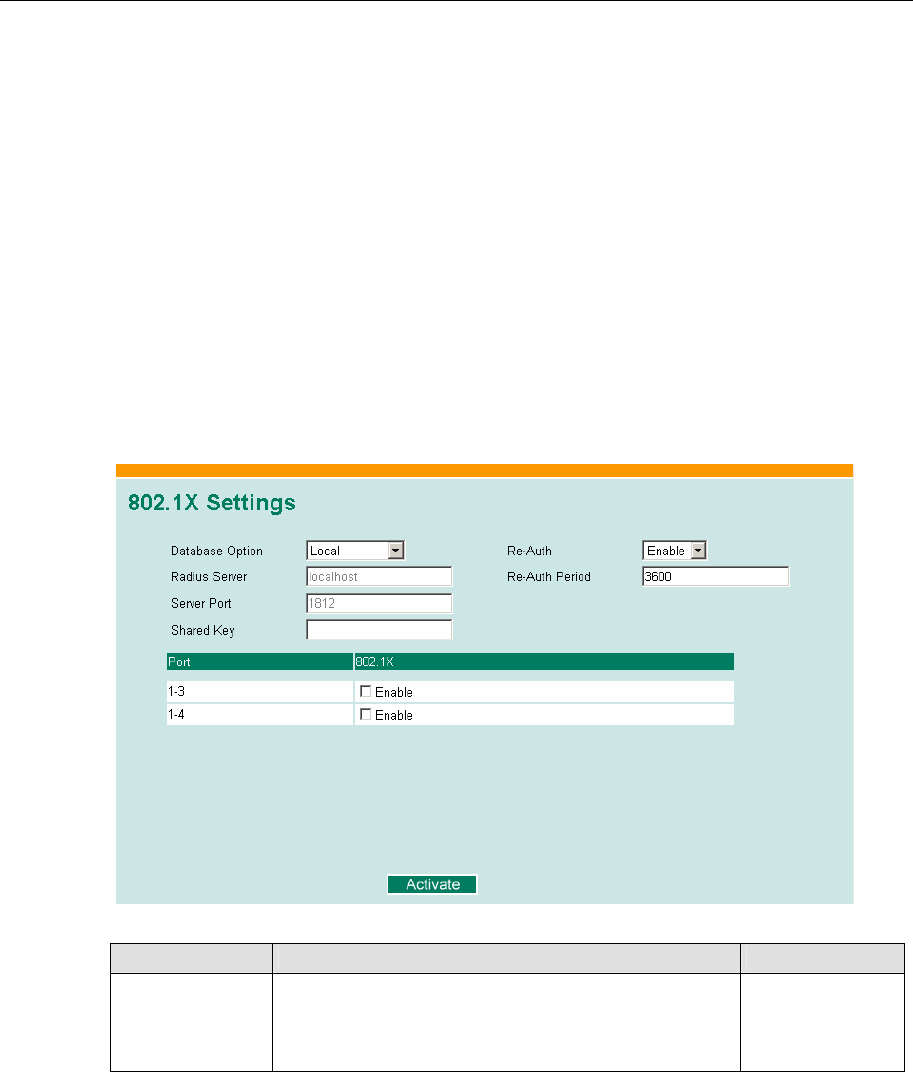
Configuring IEEE 802.1X
802.1X
Setting Description Factory Default
Enable/Disable Click the checkbox(es) under the 802.1X column to
enable IEEE 802.1X for one or more ports. All end
stations must enter usernames and passwords before
access to these ports is allowed.
Disable


















