XEROX WorkCentre
3550
Information Assurance Disclosure Paper
22
Ver. 1.3, March 2011 Page 22 of 32
5) If the LDAP Query is successful, the user’s email address is placed in the From: field. Otherwise, the
default From: is used.
6) The user may then add recipient addresses by accessing the Address Book on the LDAP server. Please
see the User Manual for details. Each addition is a separate session to the LDAP server.
3.2.2.2. SMB Authentication (Windows NT 4 or Windows 2000/Windows 2003)
This is also an option that may be enabled on the device, and is used in conjunction with scan to network
and scan to email features. The authentication steps vary somewhat, depending on the network
configuration. Listed below are 3 network configurations and the authentication steps.
Basic Network Configuration: Device and Domain Controller are on the same Subnet
Authentication Steps:
1) The device broadcasts an authentication request that is answered by the Domain Controller.
2) The Domain Controller responds back to the device whether or not the user was successfully
authenticated.
If (2) is successful, steps 3 – 5 proceed as described in steps 4 – 6 of the Kerberos section.
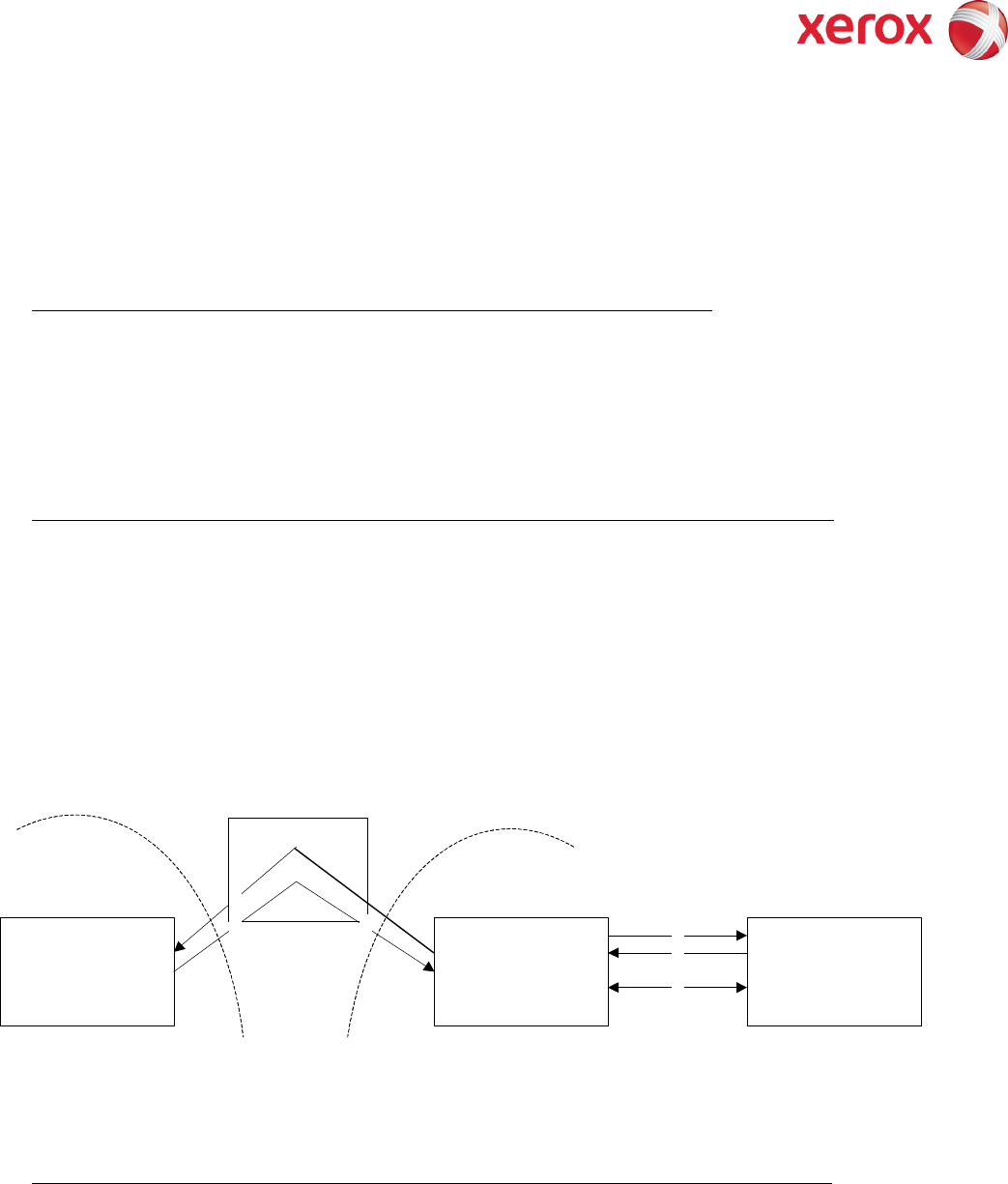
Device and Domain Controller are on different Subnets, SA defines IP Address of Domain Controller
Authentication Steps:
1) The device sends an authentication request directly to the Domain Controller through the
router using the IP address of the Domain Controller.
2) The Domain Controller responds back to the device through the router whether or not the user
was successfully authenticated.
If (2) is successful, steps 3 – 5 proceed as described in 4 - 6 of Kerberos section.
Figure 3-1 SMB Authentication with IP Address
Device and Domain Controller are on different Subnets, SA defines Hostname of Domain Controller
Authentication Steps:
Domain Controller LDAP Server
4
3
Router
1
2 2
Subnet 1
Subnet 2
WorkCentre or
WorkCentre Pro
5
1


















