38
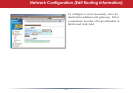
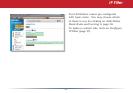
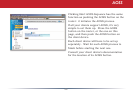
Network Configuration (Intrusion Detector)
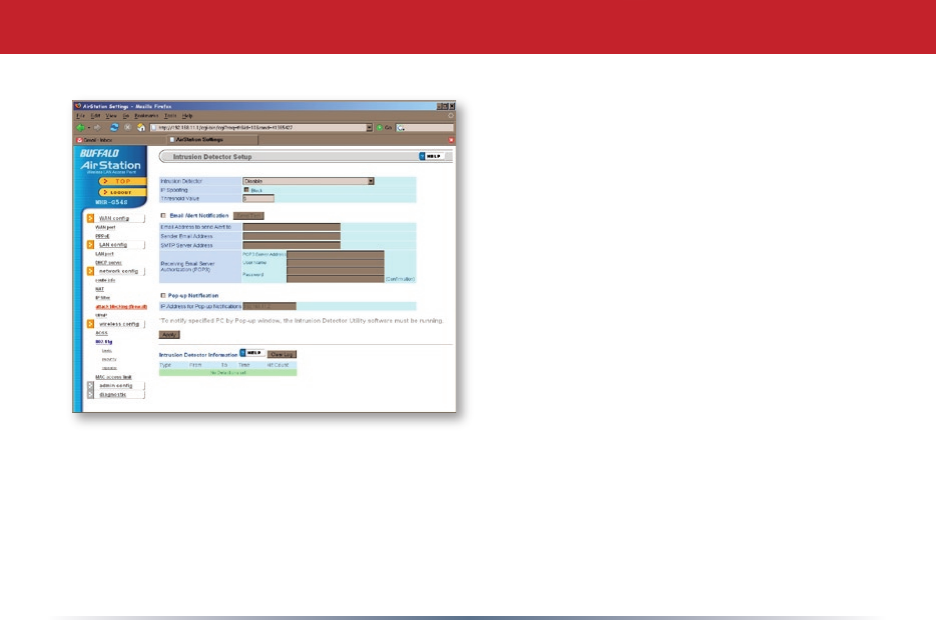
To enable intrusion detector, choose
Enable or Enable (Apply packet lter rules)
from the Intrusion Detector drop-down
box. If packet lter rules are applied,
packets will be ltered with packet lter
rules before Intrusion Detector is applied.
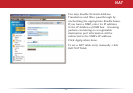
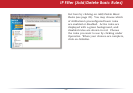
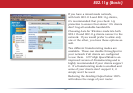
Blocking IP spoong blocks packets from
devices using an IP address that is not
their own.
In the Threshold Value box, enter the
number of times an event has to occur
before you receive notication.
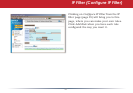
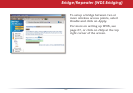
To congure your email alerts, enter your
email address and mail server information.
You may make up a sender email address,
such as “alert@router.com”. Alert emails will appear to come from this address.
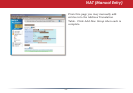
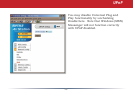
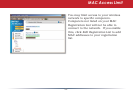
Intrusion detector also blocks unauthorized access attempts and suspicious trafc from
WAN-side devices (the internet).