Axim
™
Wireless Keyboard Owner’s Manual Page 6
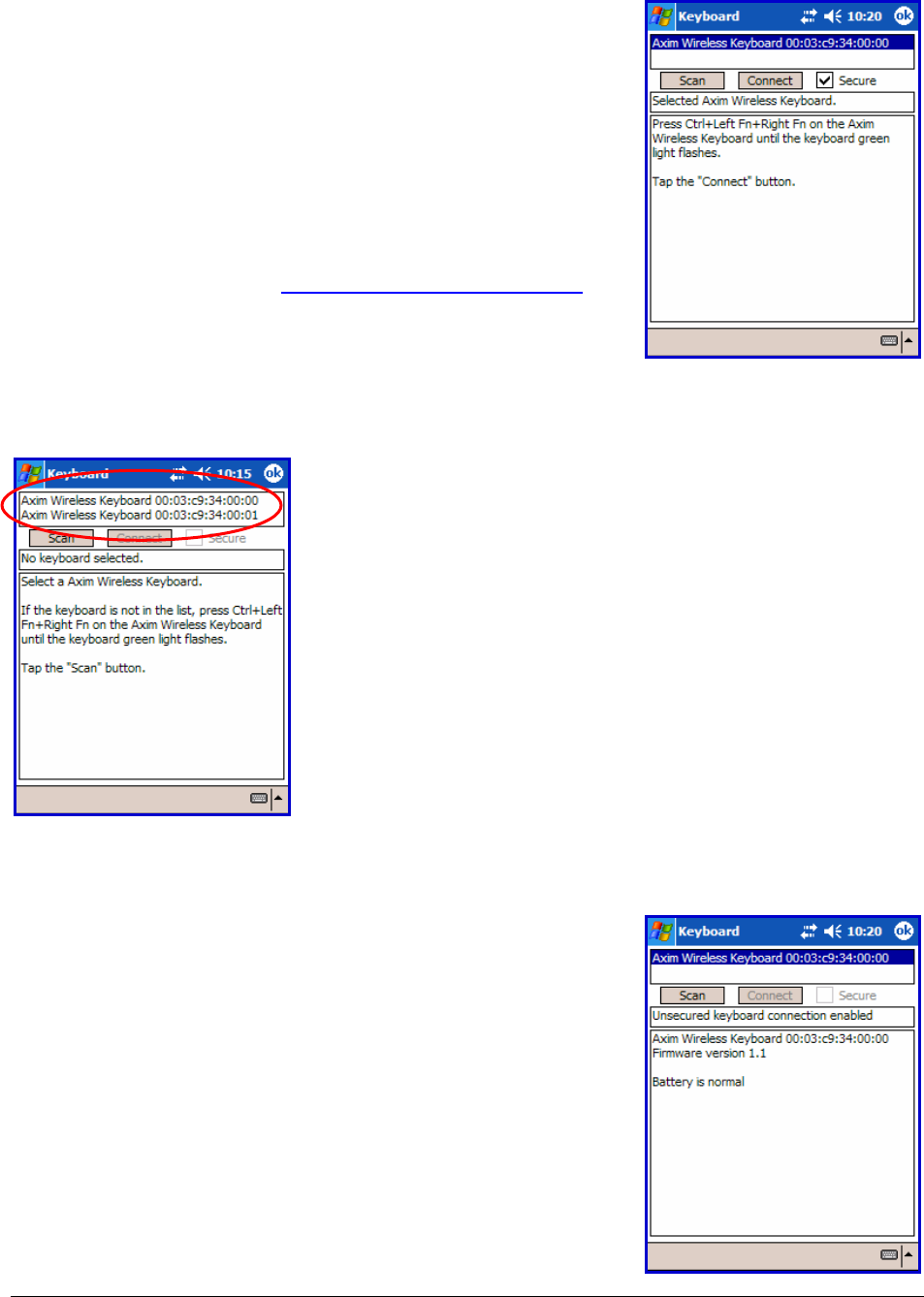
7. Once the Axim
™
Wireless keyboard appears, select
it by tapping. Then decide whether you need a secure
or unsecured connection. An unsecured connection is
vulnerable to eavesdropping. A secure connection
requires authentication by entering the same passkey
on the Pocket PC device and the keyboard (see #10).
If you prefer a secure connection, please check the
Secure box - otherwise leave it blank. Then tap the
Connect button. (See Secure Connection Overview
for more information).
8. If several Axim
™
Wireless keyboards happen to be
nearby and in Discoverable Mode, the scan will
display all of these devices in the list. The keyboard
ID (Bluetooth address) printed on the back of the
keyboard should be compared with the IDs in the list
and the desired keyboard selected.
9. If the Secure box is not checked, the connection is
usually established within a few seconds after tapping
Connect. If the connection is not established, press
the <Ctrl> Left <Fn> Right <Fn> keys together on the
keyboard and click Connect again.


















