8
EN
1
Freecom Mobile Drive Secure
1.1 Data protection by keycard (using RFID technology)
The data on the Mobile Drive Secure can be protected from unwanted access by using
a keycard to unlock the drive. This keycard is placed over a sensor inside the Mobile
Drive Secure, when the Mobile Drive Secure recognizes the keycard it will unlock the
drive for use.
The technology inside the keycard and the Mobile Drive Secure is called RFID. RFID stands
for Radio Frequency Identification. The same technology can be found for example in
office buildings, where people need to present a keycard if they want access to the
building or to a certain floor / department / room.
Your Mobile Drive Secure comes with 2 Keycards, in credit card size. This card fits easily
in your wallet so you always will carry it with you. The default setting of the drive is "no
protection". When starting to use the Mobile Drive Secure for the first time, you need to
configure the 2 supplied keycards with the drive. The Mobile Drive Secure can identify
maximum 2 keycards. We suggest that – after configuring – you use one keycard (labeled
"Security Key") and store the other keycard (labeled "Master Key") in a safe place, in case
your Security Key gets lost.
Of course you can also use the drive without the keycards. In that case you do not need
to run the configuration wizard – you can immediately start using your hard drive after
unpacking it from the box. Please note that your data is not protected against unwanted
access then.
You can also decide to use the keycard protection at a later stage, however please note
that the drive needs to be reformatted then and all data on the drive will be lost. See
chapter 4.
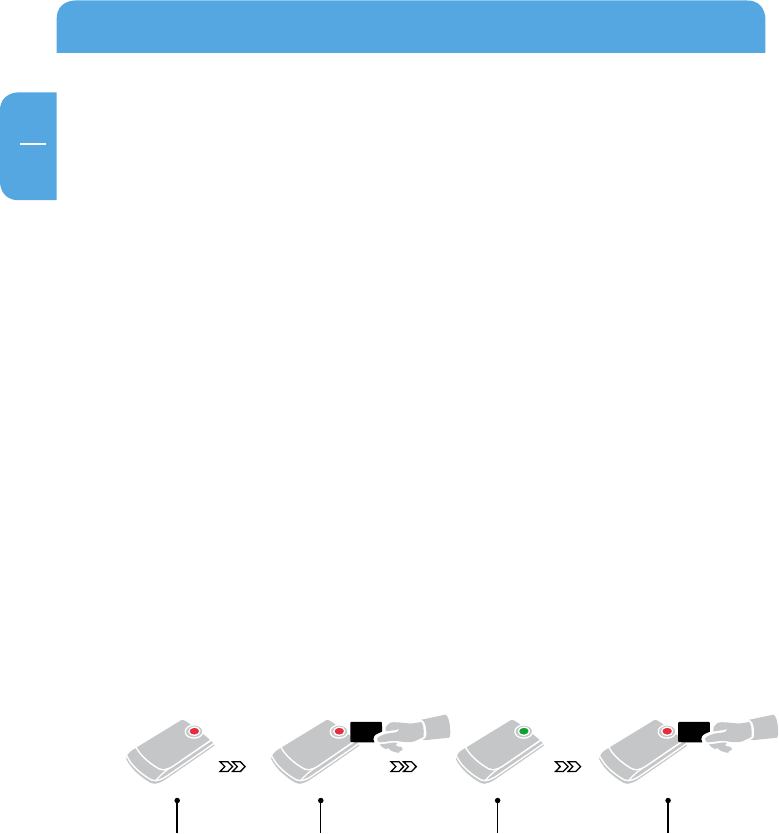
How the keycard protection works:
Mobile Drive
Secure locked
unlock Mobile Drive
Secure with keycard
over the sensor
Mobile Drive
Secure
unlocked
Move keycard over
the sensor
Mobile Drive Secure
locked
To configure the 2 keycards using the "Freecom Hard Drive Keycard Protection" software
assistant, see chapter 4.