You are recommended to run the Detector on stable CICS regions only. Do not
apply maintenance to application programs while the Detector is running. Such
maintenance may introduce or remove affinities, thus rendering collected data
inaccurate.
What is detected
The Detector detects the EXEC CICS commands listed in Table 1 on page 11 that
can cause transaction affinity. For ENQ and DEQ commands, the Detector
distinguishes between ENQ by name and ENQ by address based on the presence
of a length parameter on the EXEC CICS ENQ command. It does the same for
DEQs. The reports show which ENQs and DEQs are by name and which are by
address.
It also detects:
v The end of pseudoconversations, by detecting when one of the transactions in
the pseudoconversation terminates without issuing an EXEC CICS RETURN
TRANSID command with a non-zero transaction identifier. If a
pseudoconversation ends, and the resource shared by transactions that take part
in the affinity still exists, the lifetime of the affinity must be greater than PCONV.
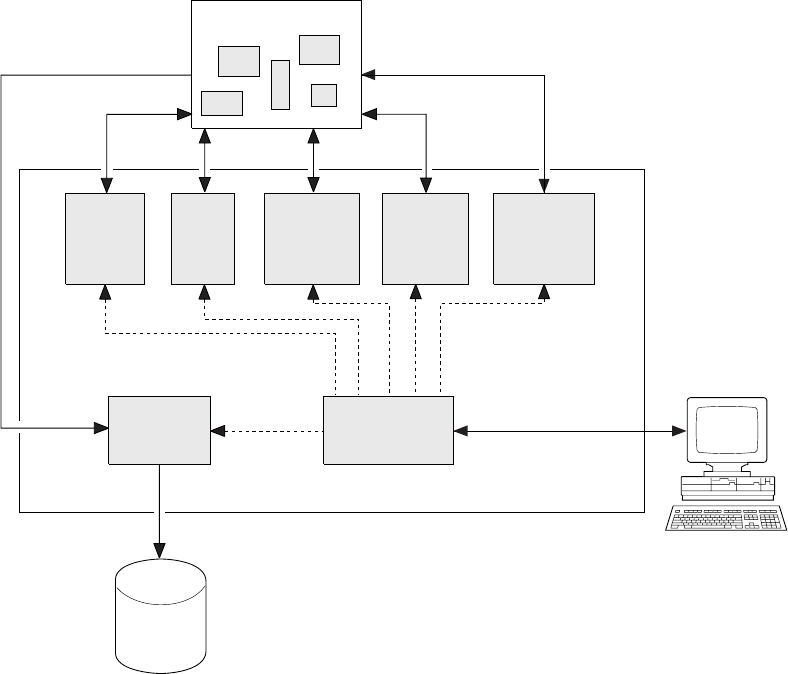
Exit
programs
User
Collected
affinity
data
Collectedaffinitydata
Dataspace
CICSAOR
or
TOR/AOR
CAFB CAFF
XEIOUT TRUE XMEOUT XICEXP
XBADEACT
Figure 3. Detector components
Chapter 2. Introducing the Transaction Affinities Utility 13
|
|
|
|
|


















