26
Chapter 5: Configuring the ADSL Gateway
The Security Tab
ADSL Gateway
• To use manual key management, select Manual, enter authentication and encryption keys (these must be
identical to those entered at the remote end), and enter inbound and outbound SPIs (security parameter
indexes). The SPIs must be exactly complementary to those entered at the remote end.
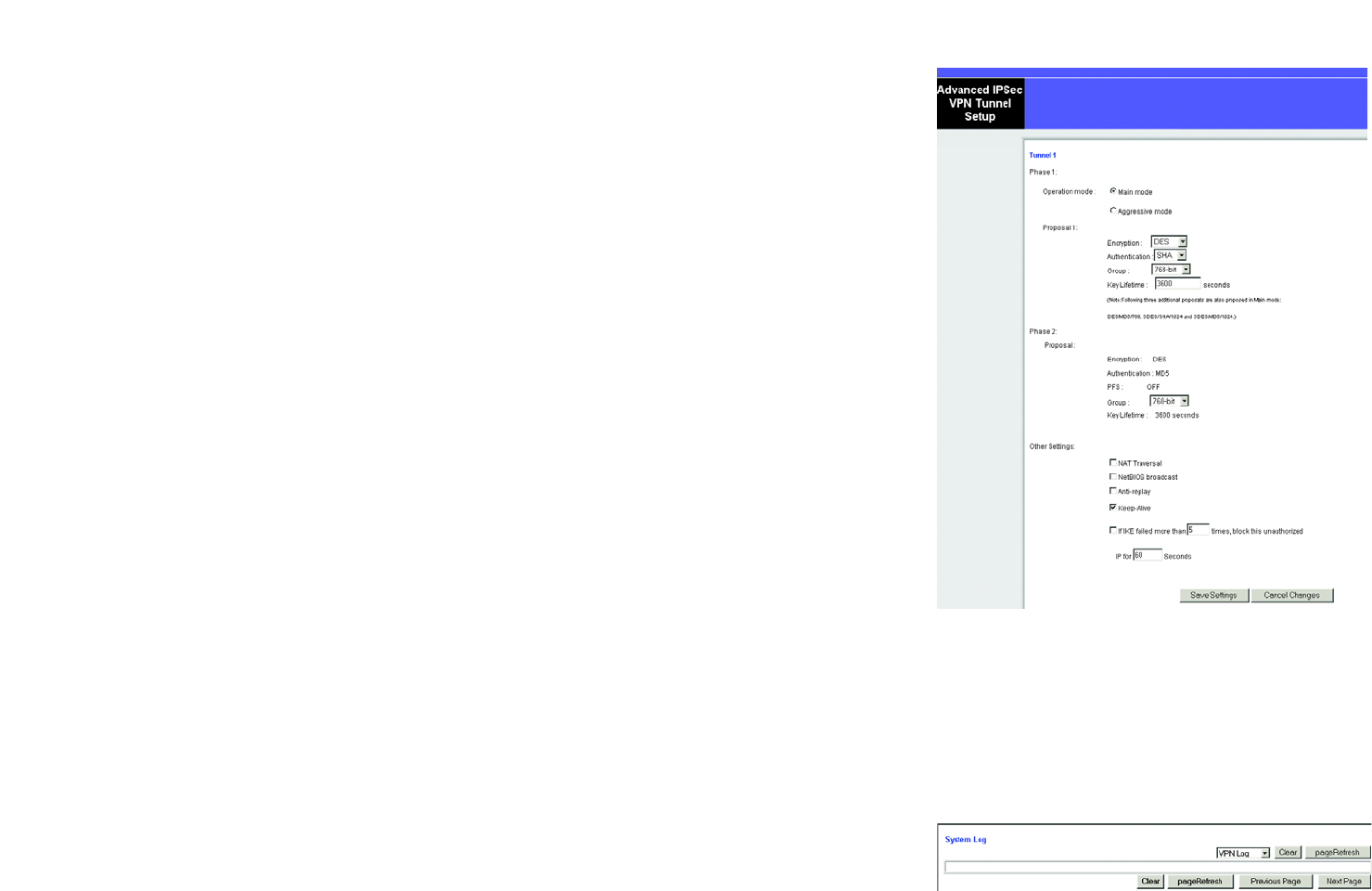
When you select automatic key management, an Advanced Settings button appears. Click this button if there are
special requirements for this IPSec tunnel. The Advanced IPSec VPN Tunnel Setup window will appear. (Help for
this window can be displayed by clicking More on the right side of the VPN panel.)
In this window you can set parameters for IKE phases 1 and 2, and other settings. Phase 1 is when the two ends
negotiate parameters for key exchange; phase 2 is when they negotiate parameters for data exchange.
• Operation mode: Key exchange parameters can be negotiated in Main mode, which is more secure, or
Aggressive mode, which is quicker. The Gateway will accept requests in either mode, but some gateways
and clients will accept requests only in the mode specified by the user.
• Proposal 1: A proposal is a set of parameters that the initiator sends and the responder examines for
acceptability. You can specify encryption and authentication algorithms, Diffie-Hellman group, and key
lifetime for the first proposal.
• Phase 2 Proposal: Select the desired Diffie-Hellman group, 768-bit or 1024-bit.
• Other Settings
NAT Traversal: Enable this feature if the machine or machines being accessed through the tunnel stand
behind a NAT (Network Address Translation) server.
NetBIOS broadcast: Enable this feature if the local network does not include a WINS server and the remote
machine or machines will need to find local machines by their NetBIOS (Windows Networking) names.
Anti-replay: Packets sent through an IPSec tunnel contain sequencing numbers to let the receiver detect if
a substitution has occurred. You can enable this function for greater security.
Keep-alive: This feature, enabled by default, makes the Gateway check the tunnel connection periodically
and attempt to re-establish it if it goes down.
If IKE failed . . . : IKE failure may signify an unwanted intrusion attempt. You can set a limit on the number
of consecutive failed requests that the Gateway will allow from the same IP address, and the amount of
time that the Gateway will ignore further requests from that address.
When finished making changes in this panel, click the Save Settings button to save your changes, or click
Cancel Changes to undo the changes. Use the VPN panel’s Connect and View Logs buttons to test the tunnel.
Figure 5-21: Advanced VPN Settings
Figure 5-22: VPN Log


















