10 NB712 / NB714 User Guide
YML829 Rev1
2.1.2 Circuit Gateway
Also called a “Circuit Level Gateway,” this is a firewall approach that validates connections before
allowing data to be exchanged. What this means is that the firewall doesn’t simply allow or disallow
packets but also determines whether the connection between both ends is valid according to
configurable rules, then opens a session and permits traffic only from the allowed source and
possibly only for a limited period of time.
2.1.3 Application Gateway
The Application Level Gateway acts as a proxy for applications, performing all data exchanges with
the remote system on their behalf. This can render a computer behind the firewall all but invisible to
the remote system. It can allow or disallow traffic according to very specific rules; permitting some
commands to a server but not others, limiting file access to certain types, varying rules according
to authenticated users and so forth. This type of firewall may also perform very detailed logging of
traffic and monitoring of events on the host system, and can often be instructed to sound alarms or
notify an operator under defined conditions. Application-level gateways are generally regarded as the
most secure type of firewall.
2.2 Denial of Service Attack
Denial of service (DoS) attacks typically come in two varieties: resource starvation and resource overload. DoS
attacks can occur when there is a legitimate demand for a resource that is greater than the supply (i.e. too many
web requests to an already overloaded web server). Software vulnerability or system misconfigurations can also
cause DoS situations. The difference between a malicious denial of service and simple system overload is the
requirement of an individual with malicious intent (attacker) using or attempting to use resources specifically to
deny those resources to other users.
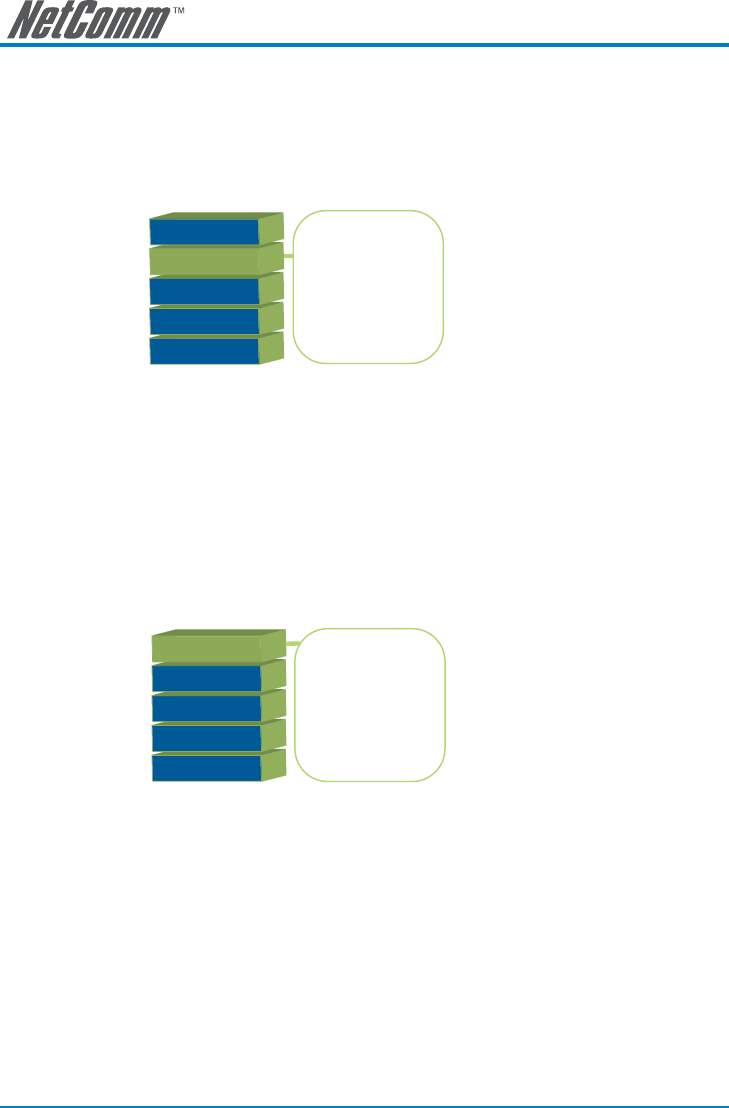
Level 5: Application
Level 4: TCP
Level 3: IP
Level 2: Data Link
Level 1: Physical
Teln et
FTP
HTT:
SMTP
Level 5: Application
Level 4: TCP
Level 3: IP
Level 2: Data Link
Level 1: Physical
Destination IP address and/
or source IP address and/or
time of day
protocol
user
password