Wireless Access Point Model 0-1591700-x User Manual Page 25 of 33
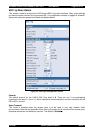
Figure 20 - WEP Key Entry Sub-Screen
Note that the identical key must be used at all the clients and at the access point, otherwise
authentication will not be possible. Keys should be changed frequently for maximum security.
802.1X
The access point can be configured to enable clients to authenticate against external RADIUS
servers using the IEEE802.1x standard. This method is best suited to corporate users where high
security is required. The 802.1x standard uses the common existing protocol, the Extensible
Authentication Protocol (EAP) for message exchange during the authentication process. The
implementation of 802.1x protocol is quite complex and needs detailed awareness of IP and
security log-on processes. This is the only setting on the access point that should only be
attempted by knowledgeable IT personnel.
In a wireless LAN with 802.1x enabled, a client requests access to an access point (known as the
authenticator). The access point forces the client into an unauthorized state that allows the client to
send only an EAP-start message. The AP replies with an EAP-request identify message to obtain
the clients identity. The clients EAP-response packet containing the clients identity is forwarded to
the RADIUS authentication server. The authentication server is configured to authenticate clients
with a specific authentication algorithm and the server returns an accept or reject packet to the
access point. Once authenticated, the access point opens the client’s port and traffic will be
forwarded.
The access point hides the complexity of the IEEE802.1x registration process as it transparently
handles the main authentication types including EAP-TLS, EAP-MD5 and EAP-TTLS. Note that all
clients in the network must use the same type of authentication.
Figure 21 - 802.1x Authentication Sub-Screen
Re-authentication Time
This value is the duration that runs before the client needs to be authenticated against the RADIUS
server.
Primary Radius Server – Authentication Server IP
This is the IP address of the primary RADIUS server. The default TCP port value is 1812. If there is
a shared secret for the transactions, then enter the value in the Shared Secret box.
PL0356 ©2003TycoElectronics Issue 1