1-8
Displaying and Maintaining ARP
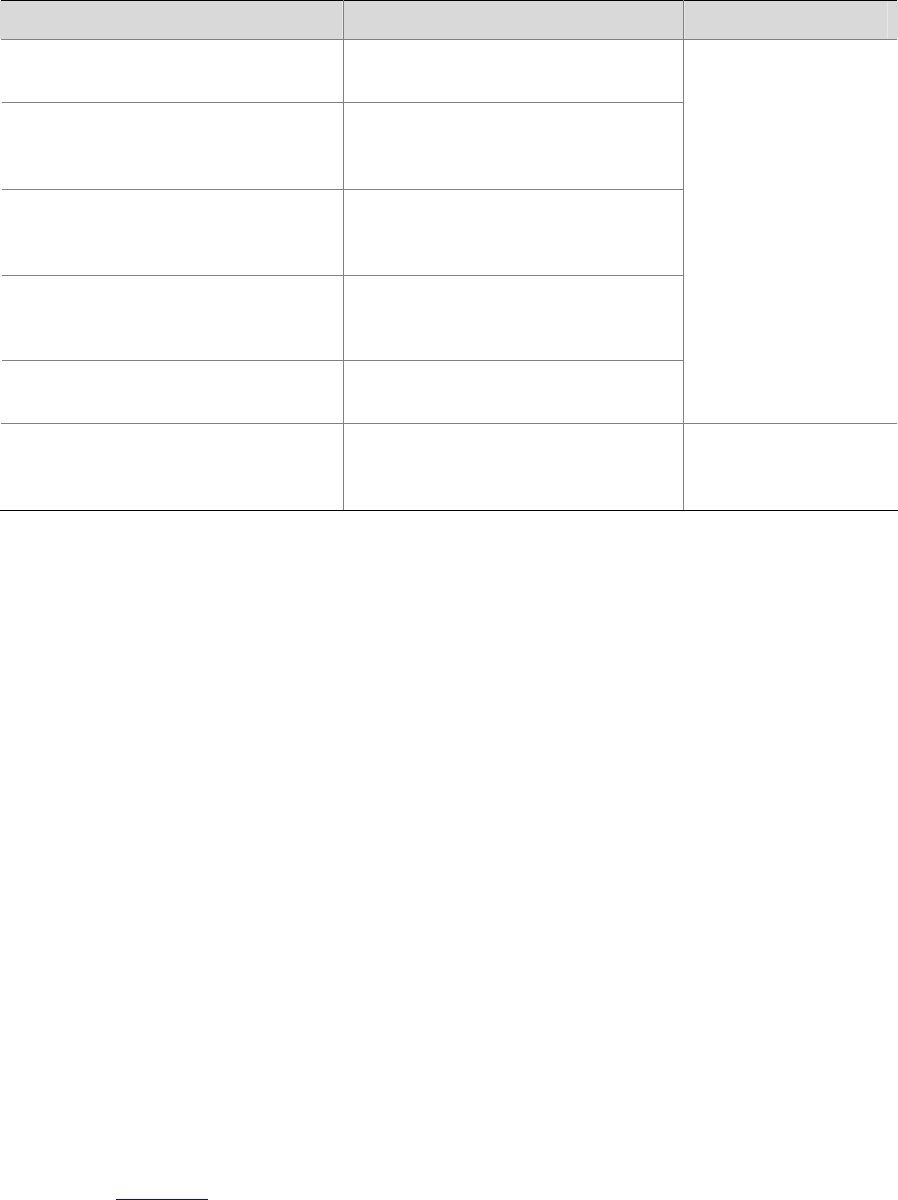
To do… Use the command… Remarks
Display specific ARP mapping table
entries
display arp [ static | dynamic |
ip-address ]
Display the ARP mapping entries
related to a specified string in a
specified way
display arp [ dynamic | static ] |
{ begin | include | exclude } text
Display the number of the ARP
entries of a specified type
display arp count [ [ dynamic |
static ] [ | { begin | include |
exclude } text ] | ip-address ]
Display the statistics about the
untrusted ARP packets dropped by
the specified port
display arp detection statistics
interface interface-type
interface-number
Display the setting of the ARP aging
timer
display arp timer aging
Available in any view
Clear specific ARP entries
reset arp [ dynamic | static |
interface interface-type
interface-number ]
Available in user view
ARP Configuration Example
ARP Basic Configuration Example
Network requirement
z Disable ARP entry check on the device.
z Set the aging time for dynamic ARP entries to 10 minutes.
z Add a static ARP entry, with the IP address being 192.168.1.1, the MAC address being
000f-e201-0000, and the outbound port being GigabitEthernet 1/0/10 of VLAN 1.
Configuration procedure
<device> system-view
[device] undo arp check enable
[device] arp timer aging 10
[device] arp static 192.168.1.1 000f-e201-0000 1 gigabitethernet 1/0/10
ARP Attack Detection Configuration Example
Network requirements
As shown in Figure 1-4, GigabitEthernet 1/0/1 of Switch A connects to DHCP Server; GigabitEthernet
1/0/2 connects to Client A, GigabitEthernet 1/0/3 connects to Client B. GigabitEthernet 1/0/1,
GigabitEthernet 1/0/2 and GigabitEthernet 1/0/3 belong to VLAN 1.
z Enable DHCP snooping on Switch A and specify GigabitEthernet 1/0/1 as the DHCP snooping
trusted port.
z Enable ARP attack detection in VLAN 1 to prevent ARP man-in-the-middle attacks, and specify
GigabitEthernet 1/0/1 as the ARP trusted port.


















