8
Back to My Mac User’s Guide
December 2007
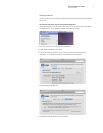
Check rewall settings if you cannot connect
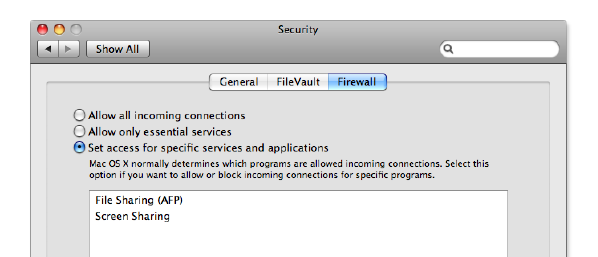
MacOSXLeopardhasabuilt-inrewall,whichisaccessiblefromtheFirewalltabof
yourSecuritypreferences.Youshouldverifythattherewallissettoeither“Allowall
incomingconnections”or“Setaccessforspecicservicesandapplications.”
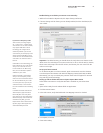
Ifyouuseathird-partyrewall,youmayneedtomodifythecongurationtopermit
BacktoMyMactofunctioncorrectly.Insomecorporate(ormanaged)networkenvi-
ronments, you may need to consult your system administrator. When signing in to
.MacandenablingBacktoMyMac,TCPport443isused.Forconnectionsbetween
machines,BacktoMyMactypicallyusesUDPport4500.
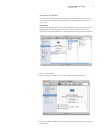
Security
Back to My Mac uses advanced authentication and security technologies to help
prevent unauthorized access to your data and protect it while it is in transit over the
Internet.Whenyourstsigninto.MaconasystemrunningLeopard,youreceivea
digitalcerticateandprivatekeyforyour“.MacSharingIdentitity.”Whenyouconnect
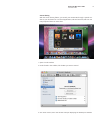
to another system using Back to My Mac, authentication is performed using the stan-
dardPublicKeyCryptographyforInitialAuthenticationinKerberos(PKINIT)protocol
withthe.Macsharingidentity.CommunicationbetweenBacktoMyMaccomputers
over the public Internet is encrypted using IPSec.
For More Information
For more information about Back to My Mac and other .Mac services,
visit www.apple.com/dotmac.
©2007AppleInc.Allrightsreserved.Apple,theApplelogo,AirPortExpress,AirPortExtreme,iMac,iPhoto,
Keynote,Mac,MacBook,andMacOSaretrademarksofAppleInc.,registeredintheU.S.andothercountries.
FinderandLeopardaretrademarksofAppleInc..MacisaservicemarkofAppleInc.,registeredintheU.S.and
othercountries.Thismaterialisprovidedforinformationpurposesonly;Appleassumesnoliabilityrelatedtoits
use.November2007L358808A