14
3. Network Functions
&RQ¿JXULQJDQGFRQWUROOLQJWKHSURMHFWRUYLDDZHEEURZVHUFRQWLQXHG
3.1.1 Logon
5HIHUWRWKHIROORZLQJIRUFRQ¿JXULQJRUFRQWUROOLQJWKHSURMHFWRUYLDDZHEEURZVHU
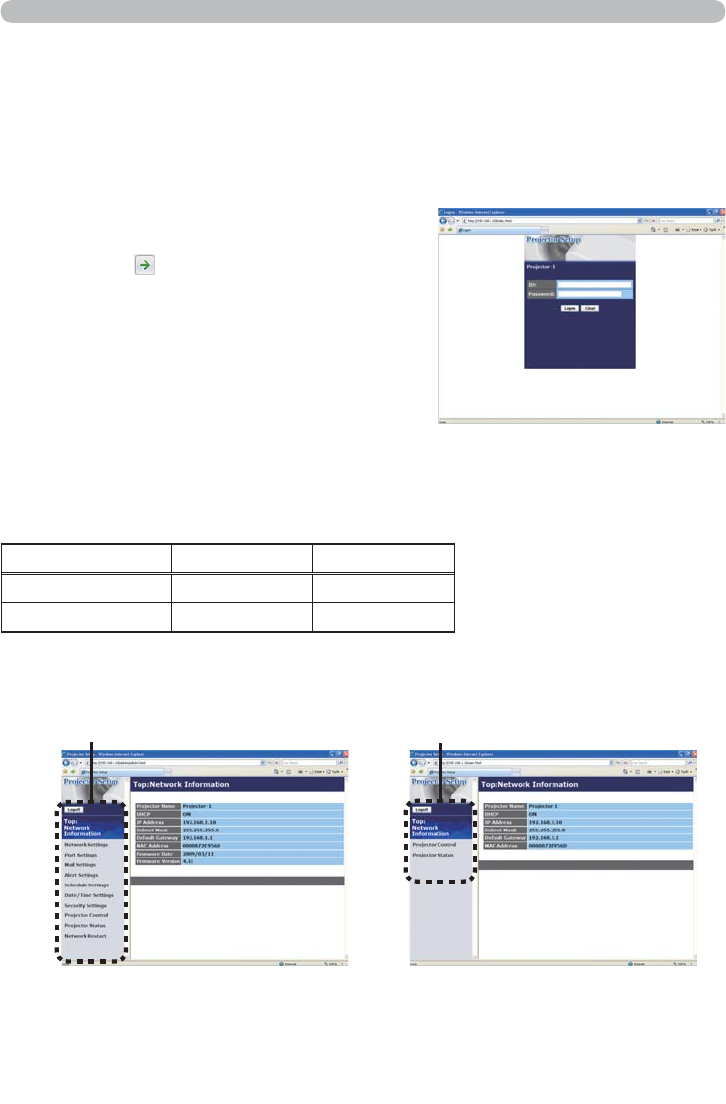
(QWHU“http://192.168.1.10/”LQWRWKHDGGUHVV
EDURIWKHZHEEURZVHUDQGSUHVV³(QWHU´
NH\RUFOLFN³
´EXWWRQ7KHVFUHHQLQ)LJ
DZLOOEHGLVSOD\HG
(QWHU\RXU,'DQGSDVVZRUGDQGFOLFN
[Logon]
Example,IWKH,3DGGUHVVRIWKHSURMHFWRULVVHWWR192.168.1.10:
)LJD³/RJRQ0HQX´
%HORZDUHWKHIDFWRU\GHIDXOWVHWWLQJVIRU$GPLQLVWUDWRU,'8VHU,'DQGSDVVZRUGV
Item ID Password
$GPLQLVWUDWRU $GPLQLVWUDWRU EODQN!
8VHU 8VHU EODQN!
,IWKHORJRQLVVXFFHVVIXOHLWKHUWKH)LJERU)LJFVFUHHQZLOOEH
GLVSOD\HG
)LJE³/RJRQZLWK$GPLQLVWUDWRU,'´
0DLQPHQX
)LJF³/RJRQZLWK8VHU,'´
0DLQPHQX
&OLFNWKHGHVLUHGRSHUDWLRQRUFRQ¿JXUDWLRQLWHPRQWKHPDLQPHQXORFDWHGRQ
WKHOHIWKDQGVLGHRIWKHVFUHHQ


















