Level
3
PUSH
Level
2
CALL
Level
2:
-E
N
TE
R
MOV
ARPL
PROTECTION
SELECTOR
LEVEL
2
4 , 0
AX,
[BPJ+4
[BPJ+6,
AX
RPL
value
doesn't
matter
at
level
3
GET
CS
of
return
address,
RPL=3
Put 3
in
RPL
field
PUSH
WORD
PTR
[BPJ+6j
Pass
selector
CALL
Level
0
Level
0:
-E
N
TE
R
Level
0
MOV
ARPL
6,0
AX,
[BPJ+4
[BPJ+6,
AX
Get
CS
of
return
address,
RPL=2
Leaves
RPL
unchanged
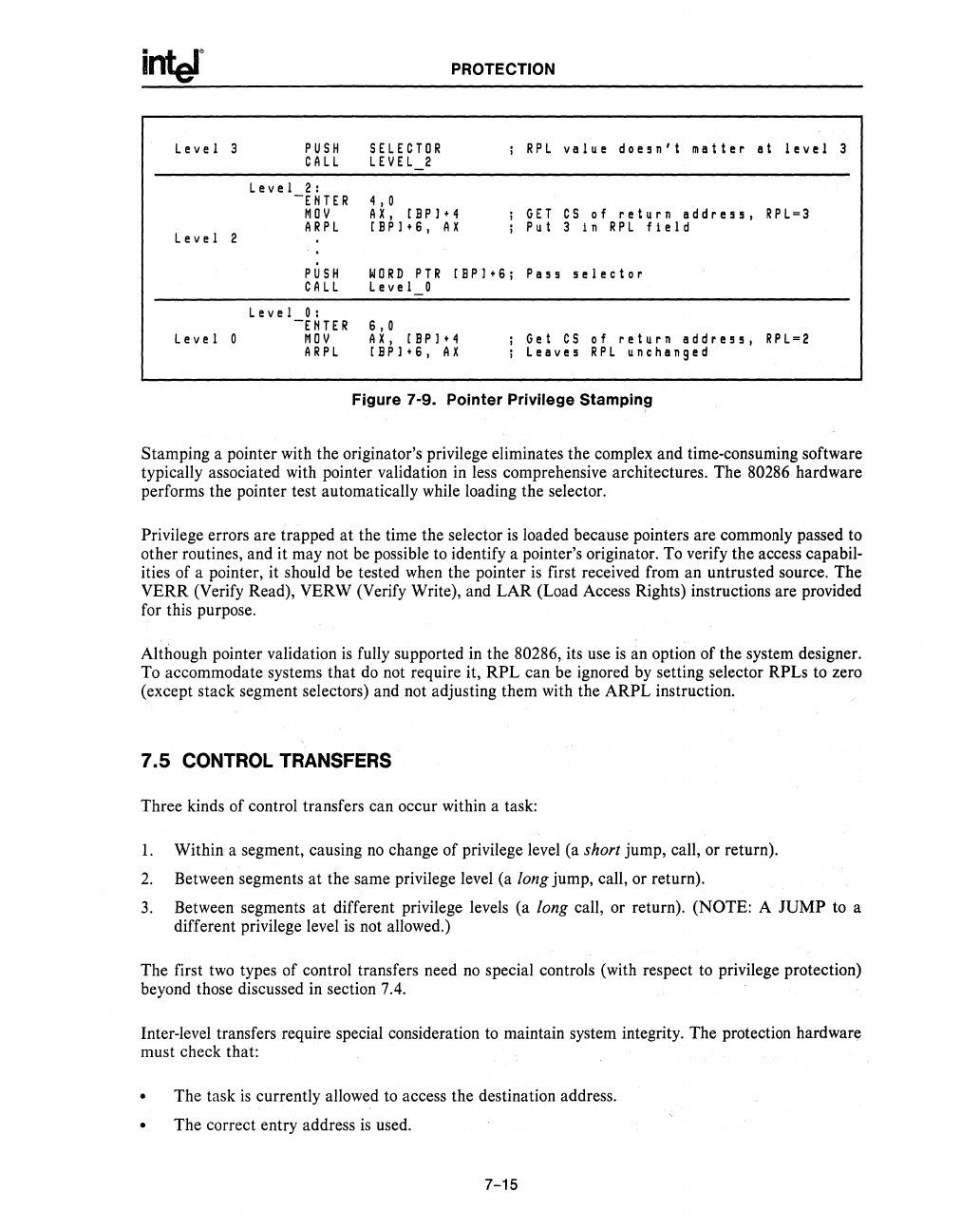
Figure 7-9. Pointer Privilege Stamping
Stamping a pointer with the originator's privilege eliminates the complex and time-consuming software
typically associated with pointer validation in
less
comprehensive architectures. The 80286 hardware
performs the pointer test automatically while loading the selector.
Privilege errors are trapped at the time the selector
is
loaded because pointers are commonly passed to
other routines, and it may not be possible
to
identify a pointer's originator. To verify the access capabil-
ities of a pointer, it should be tested when the pointer
is
first received from an untrusted source. The
VERR (Verify Read), VERW (Verify Write), and LAR (Load Access Rights) instructions are provided
for this purpose.
Although pointer validation
is
fully supported in the 80286, its use
is
an option of the system designer.
To accommodate systems that
do
not require it,
RPL
can be ignored by setting selector RPLs to zero
(except stack segment selectors) and not adjusting them with the ARPL instruction.
7.5
CONTROL TRANSFERS
Three kinds of control transfers can occur within a task:
1.
Within a segment, causing
no
change of privilege level (a short jump, call, or return).
2.
Between segments at the same privilege level (a long jump, call, or return).
3.
Between segments at different privilege levels (a long call, or return). (NOTE: A
JUMP
to a
different privilege level
is
not allowed.)
The first two types of control transfers need
no
special controls (with respect to privilege protection)
beyond those discussed in section 7.4.
Inter-level transfers require special consideration to maintain system integrity. The protection hardware
must check that:
The task
is
currently allowed to access the destination address.
The correct entry address
is
used.
7-15


















