Starting Forensic Analysis using Snort rules
Chapter 6 Forensic Analysis using Snort
98
rev. 1
10 Click OK to close the Forensic Analysis Profile dialog. Click OK
again to close the Forensic Settings dialog. Click OK to close the
GigaStor Analysis Options dialog.
Observer applies the rules and filters to the capture data and
displays the results in the Forensics Summary tab. A new tab is
also opened that contains the decode. For details about the tabs,
see:
Q “About Forensic Analysis tab” on page 98
Q “About the Forensic Analysis Log tab” on page 99
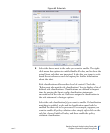
About Forensic Analysis tab
This display summarizes alerts and preprocessor events in a navigable
tree.
Figure 70 Forensic Summary
T
IP! PREPROCESSOR
MAXIMUMS
It is important to examine the preprocessor results to ensure
that time-outs and other maximum value exceeded conditions
haven’t compromised the analysis. In Figure 70, both the IP
Flow and TCP Stream Reassembly preprocessors have timed
out on hundreds of flows and streams. If you see similar