IDP Support Notes
5
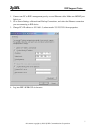
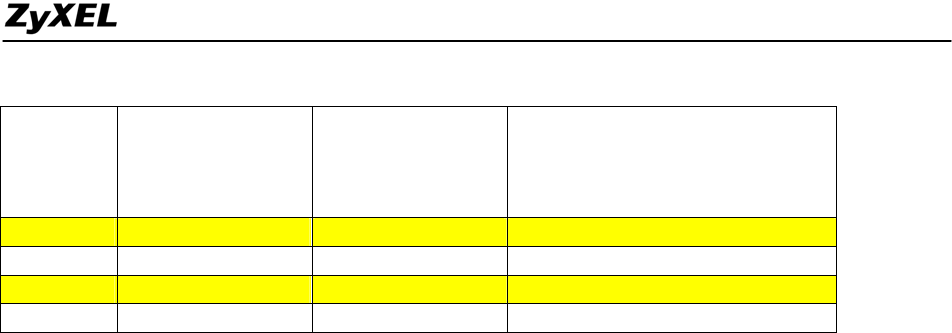
Servers/PC 192.168.2.5-10 LAN1: 192.168.1.5-50
LAN2: 192.168.1.51-100
WLAN: 192.168.1.101-130
Data Center: 192.168.1.131-140
Device IDP (A) IDP (B) IDP (C)
IP Address 192.168.1.141 192.168.1.142 192.168.1.143
Device IDP (D) IDP (E) IDP (F)
IP Address 192.168.1.144 192.168.1.145 192.168.1.146
Purpose:
IDP (A)
Since network devices may also have vulnerabilities, once the firewall device at gateway is
compromised, the protected networks are also endangered. The IDP device outside firewall can
block attacks to firewall/VPN gateways from Internet. So we apply policy protection on WAN
port of IDP (A).
IDP (B)
Servers in DMZ zone are the most critical point in your network. Since malicious attacks may
flow into DMZ along with legitimate traffic. The attacks may come from Internet and to prevent
the infected server from attacking internal networks, so we apply policy protection on both WAN
and LAN port of IDP (B).
IDP (C), IDP (D)
The purpose of IDP (C) and IDP (D) is to separate internal network into blocks, and thus once a
PC gets infected by some worms/virus, the infection won’t spread into the whole network.
Therefore we apply policy protection on both WAN and LAN port of IDP (C) and IDP (D).
IDP (E)
Since IDP (E) protects the data center of the network, and we assume data center is always
waiting for internal users to access, there are no connections initiated from the data center area.
We apply policy protection on WAN port of IDP (E).
IDP (F)
Wireless LAN is a popular application nowadays due to its mobility. However, WLAN does raise
some security concerns into network applications also because of its mobility. Administrators
can’t predict when a mobile notebook will be cracked, and trying to spread worms/virus through
WLAN. So we suggest users to place an IDP device before WLAN connects to internal network.
The policy protection applies on LAN port of IDP (F).
All contents copyright (c) 2004 ZyXEL Communications Corporation.