160 Brocade ICX 6650 Security Configuration Guide
53-1002601-01
How 802.1X port security works
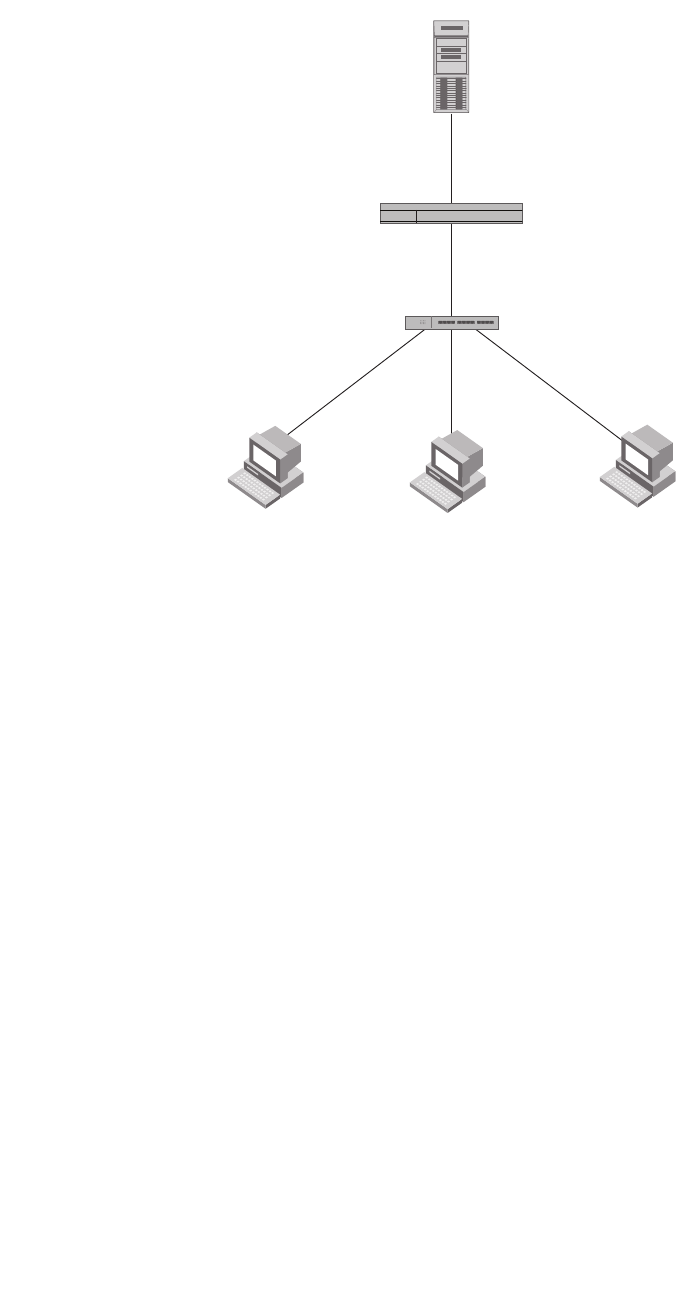
FIGURE 5 Multiple hosts connected to a single 802.1X-enabled port
If there are multiple hosts connected to a single 802.1X-enabled port, the Brocade device
authenticates each of them individually. Each host authentication status is independent of the
others, so that if one authenticated host disconnects from the network, it has no effect on the
authentication status of any of the other authenticated hosts.
By default, traffic from hosts that cannot be authenticated by the RADIUS server is dropped in
hardware. You can optionally configure the Brocade device to assign the port to a “restricted” VLAN
if authentication of the Client is unsuccessful.
How 802.1X multiple-host authentication works
When multiple hosts are connected to a single 802.1X-enabled port on a Brocade device (as in
Figure 5), 802.1X authentication is performed in the following way.
1. One of the 802.1X-enabled Clients attempts to log into a network in which a Brocade device
serves as an Authenticator.
2. The Brocade device creates an internal session (called a dot1x-mac-session) for the Client. A
dot1x-mac-session serves to associate a Client MAC address and username with its
authentication status.
3. The Brocade device performs 802.1X authentication for the Client. Messages are exchanged
between the Brocade device and the Client, and between the device and the Authentication
Server (RADIUS server). The result of this process is that the Client is either successfully
authenticated or not authenticated, based on the username and password supplied by the
client.
4. If the Client is successfully authenticated, the Client dot1x-mac-session is set to
“access-is-allowed”. This means that traffic from the Client can be forwarded normally.
RADIUS Server
(Authentication Server)
Brocade Switch
(Authenticator)
Clients/Supplicants running 802.1X-compliant client software
e1/2/1
192.168.9.22
Hub


















