24-2
Catalyst 2950 and Catalyst 2955 Switch Software Configuration Guide
OL-10101-02
Chapter 24 Configuring SPAN and RSPAN
Understanding SPAN and RSPAN
Figure 24-1 Example SPAN Configuration
Only traffic that enters or leaves source ports can be monitored by using SPAN.
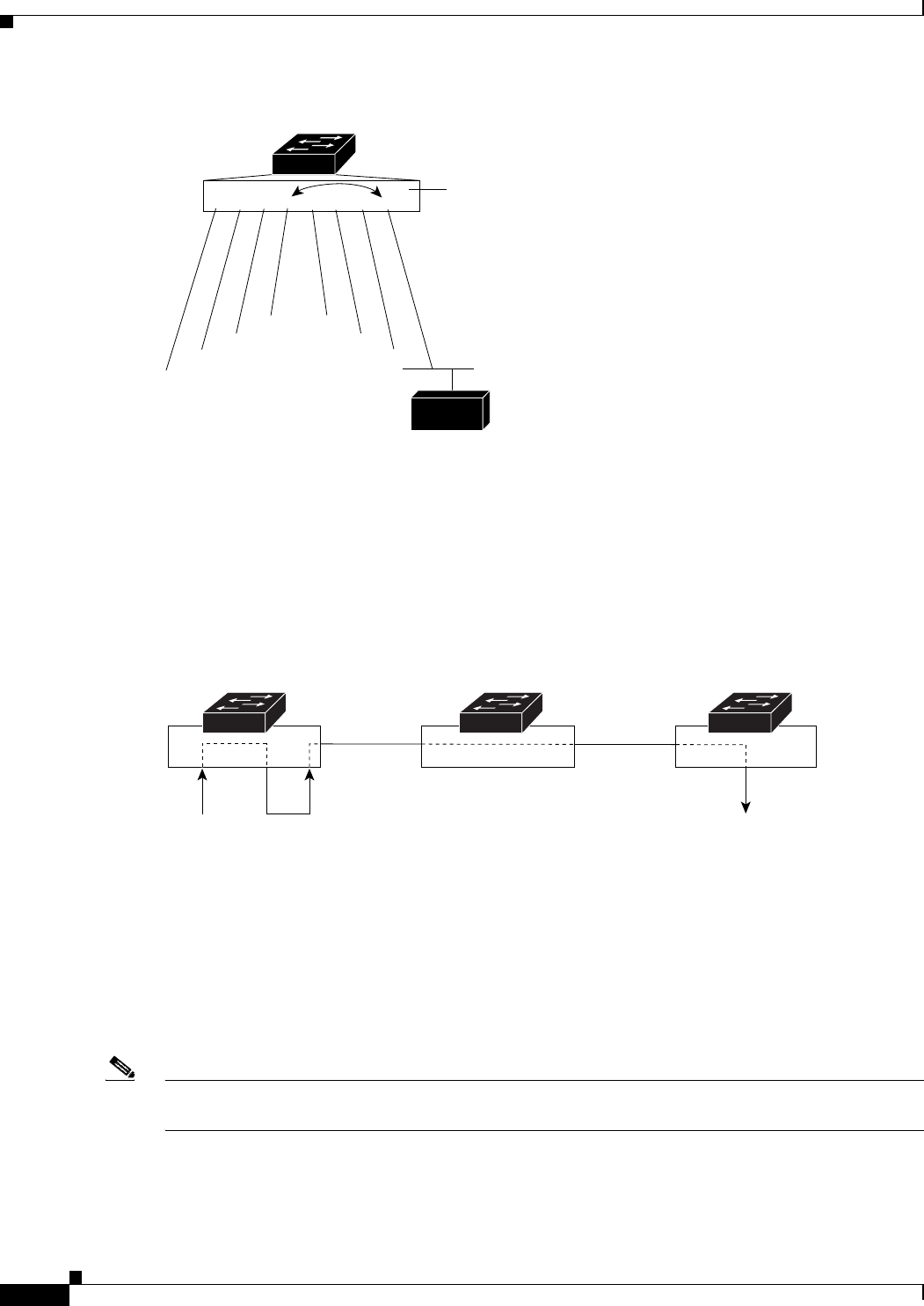
RSPAN extends SPAN by enabling remote monitoring of multiple switches across your network. The
traffic for each RSPAN session is carried over a user-specified RSPAN VLAN that is dedicated for that
RSPAN session in all participating switches. The SPAN traffic from the sources is copied onto the
RSPAN VLAN through a reflector port and then forwarded over trunk ports that are carrying the RSPAN
VLAN to any RSPAN destination sessions monitoring the RSPAN VLAN, as shown in
Figure 24-2.
Figure 24-2 Example of RSPAN Configuration
SPAN and RSPAN do not affect the switching of network traffic on source ports; a copy of the packets
received or sent by the source interfaces are sent to the destination interface. Except for traffic that is
required for the SPAN or RSPAN session, reflector ports and destination ports do not receive or forward
traffic.
You can use the SPAN destination port to inject traffic from a network security device. For example, if
you connect a Cisco Intrusion Detection System (IDS) Sensor Appliance to a destination port, the IDS
device can send TCP Reset packets to close down the TCP session of a suspected attacker.
Note You cannot use the RSPAN destination port to inject traffic from a network security device. The switch
does not support ingress forwarding on an RSPAN destination port.
1 2 3 4 5 6 7 8 ...
Port 4 traffic mirrored
on Port 8
3
2
1
4
5
7
8
6
Network analyzer
111414
Source switch Intermediate switch Destination switch
74727
RSPAN
source port
RSPAN
destination port
Reflector
port
RSPAN
VLAN
RSPAN
VLAN


















